The reality is that, while SaaS application vendors build in a fair amount of security in their solutions, a few things can get in the way:
- Humans: Decisions we defer and mistakes we make all add up to vulnerabilities.
- Manual processes: Related to the first, there are always going to be gaps in handoffs and steps missed.
- Misaligned expectations: Also related to the first, there is a disconnect between what vendors believe is their obligation versus what customers expect.
When a SaaS data compromise occurs, all three are often at play, and it’s important to recognize that there is shared responsibility between cloud providers and their customers, and there are best practices that can be applied to minimize the risks associated with SaaS applications.
A Little Context
Recently, a targeted credential theft campaign impacted several customers of a major SaaS provider, resulting in a SaaS data compromise. Despite the severity of these incidents, the breaches were not due to any vulnerability or misconfiguration in their platform. Instead, threat actors exploited stolen credentials from users who had not enabled multi-factor authentication (MFA), leveraging these to access sensitive data.
What is the SaaS Vendor’s Responsibility?
Most SaaS vendors offer comprehensive measures and frameworks designed to protect data. This includes providing guidance on best practices such as enabling MFA and restricting network access to trusted locations. However, the responsibility for implementing these measures ultimately lies with the customers. The vendor’s role is to supply the necessary security infrastructure, but it is up to each organization to deploy and enforce these controls effectively.
Could DSPM Have Made a Difference?
Since I work for a Data Security Posture Management (DSPM) vendor, we review every breach to determine if our solution could have mitigated the impact of these breaches… or prevented them entirely.
Here are steps that can be taken to mitigate the likelihood of credential theft happening:
Credential Management
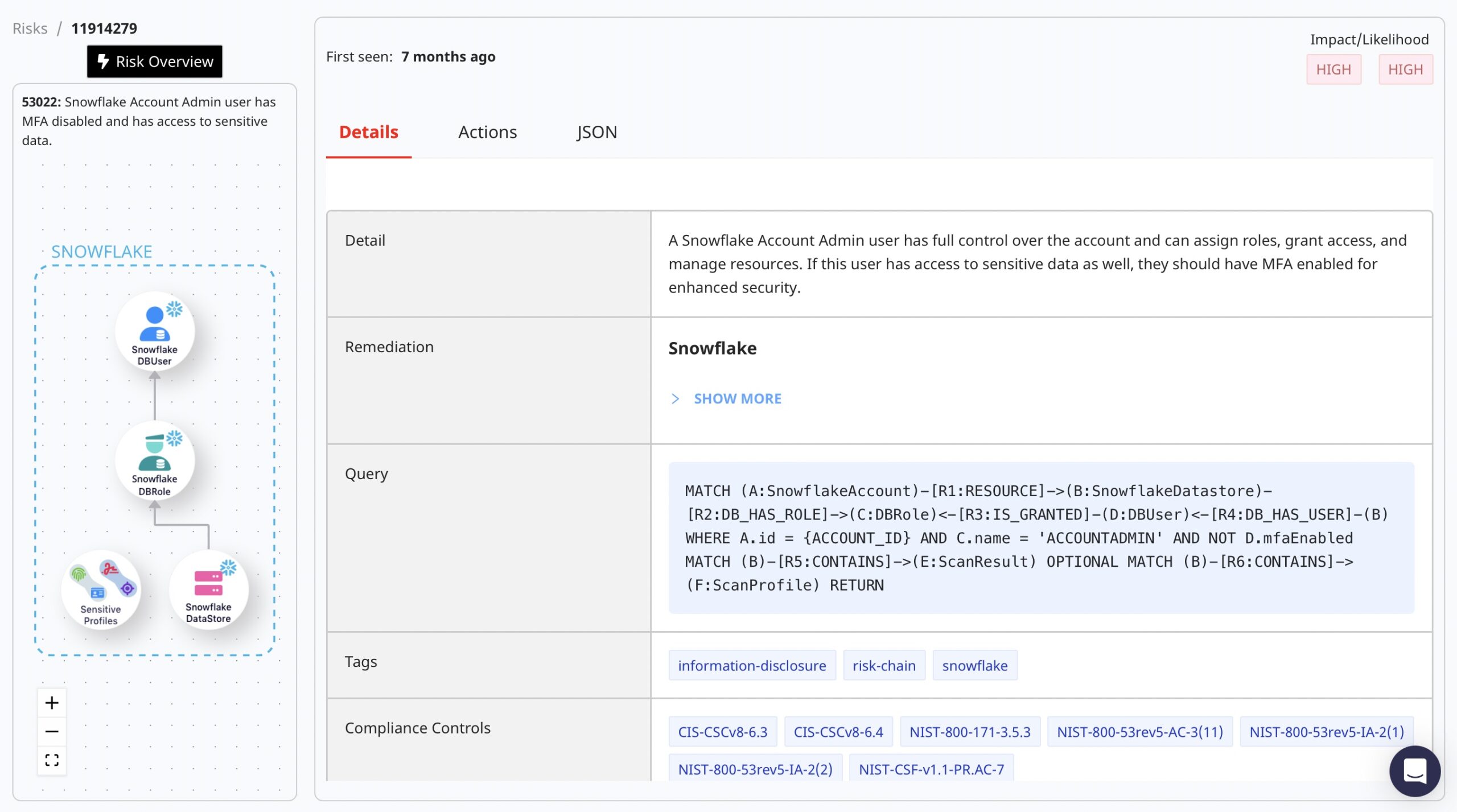
DSPM tools like Normalyze can identify users with access to sensitive data who lack necessary security measures like MFA. By flagging these users and enforcing stricter authentication policies, the risk of unauthorized access can be significantly reduced.
Anomaly Detection
Continuous monitoring provided by Normalyze can detect unusual activity patterns, such as unexpected data download spikes or access from atypical locations. These anomalies can trigger alerts, enabling security teams to respond promptly and potentially prevent data breaches.
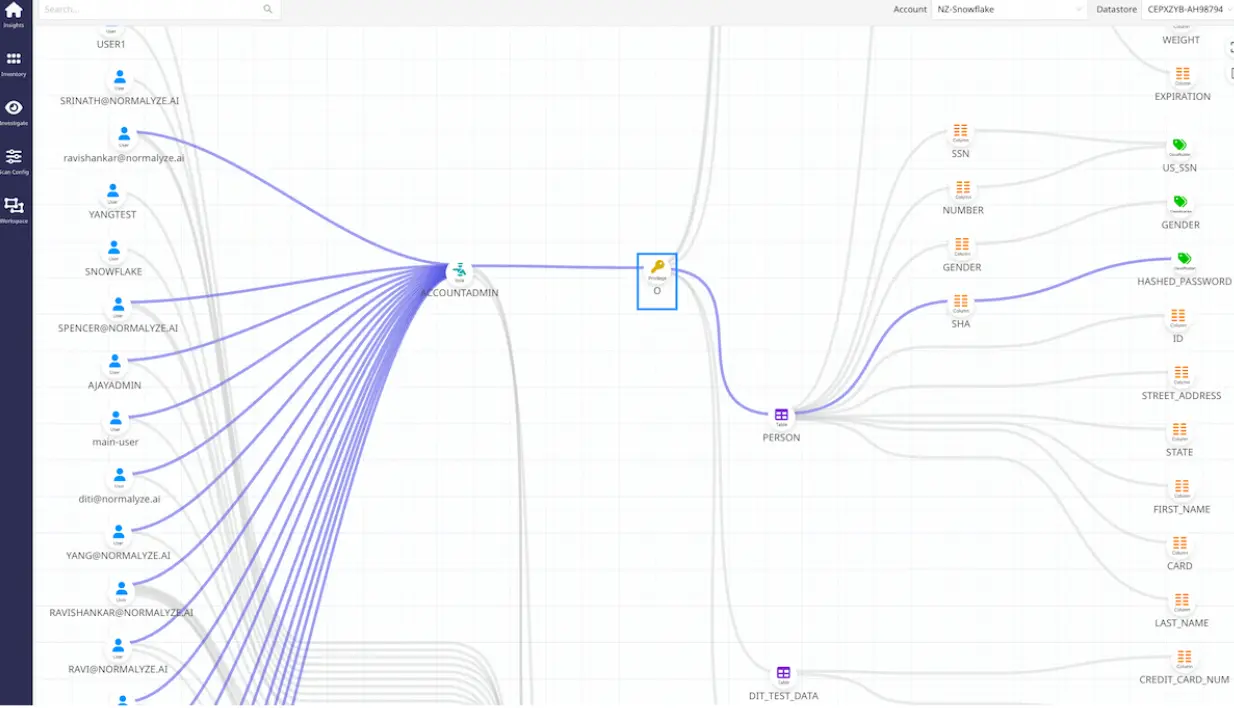
Data Risk Paths
Normalyze visualizes data risk paths, highlighting misconfigurations or excessive permissions that increase vulnerability. As quickly as data is created and moves, Normalyze can see who is trying to access it and how.
Data Classification
This is the foundation to better data security, more broadly than this use case. By classifying data, teams can focus on the data stores that contain valuable or sensitive information like Personally Identifiable Information (PII). Why boil the ocean when you can zero in on just the most critical data you need to secure.
Best Practices
With or without Normalyze, here are eight things we recommend you consider doing today:
1. Classify and Tag Sensitive Data
Ensure all sensitive data is correctly classified and tagged. This foundational practice sets the stage for managing access controls more effectively, and ensuring that only authorized users have access to critical information.
2. Prioritize Security Based on Data Access
Focus your security resources on users who have access to valuable or sensitive data. By identifying the data you are trying to protect, you can spot users with excessive permissions and ensure your security efforts are directed where they are most needed.
3. Enforce Least Privilege Access
Apply the principle of least privilege by ensuring users have the minimum level of access necessary for their roles. This reduces the risk of unauthorized access and potential data breaches.
4. Identify Users with Inadequate Security Measures
Use our DSPM platform to swiftly identify Snowflake users who have access to sensitive data but lack MFA. Enabling MFA for these users is a fundamental step in bolstering your data security.
5. Manage Inactive Users to Reduce Risk
Leverage Normalyze Access Graphs to continuously identify inactive or dormant users who still retain access to sensitive data. Reduce their permissions or disable these accounts to minimize potential security risks. This step helps in narrowing the scope of access and reducing the potential impact of a breach.
6. Monitor and Detect Anomalous Activity
Implement continuous monitoring to identify unusual activity patterns. Normalyze alerts you to anomalies such as data access from unexpected locations or unusual spikes in data downloads, enabling timely responses to potential threats.
7. Regularly Review and Update Security Policies
Continuously review and update your security policies to keep up with evolving threats. DSPM platforms automate the process of validating compliance with security policies, ensuring your organization is always prepared.
8. Leverage Automation and AI to Continuously Perform Steps 1-7 🙂
Ask Normalyze to automate these steps along with compliance and security checks. Regular automated scans help identify and remediate security gaps promptly, maintaining a robust security posture.
Follow these best practices to reduce the risk of a SaaS data compromise.