TRUSTED BY
Do you know…
If you can’t answer these questions, you need Normalyze.
With thousands of data security tools in the market, data breaches continue to happen on a daily basis.
To solve this problem, Normalyze takes a data-first approach to security. Normalyze is the pioneer of Data Security Posture Management (DSPM), helping global enterprises secure their data across Cloud, SaaS, PaaS, on-premises and hybrid environments.
By understanding where valuable and sensitive data is, the resources that access it, and how it is being used, data and security teams can collaborate on security and governance plans that make sense for the business.
How
it Works
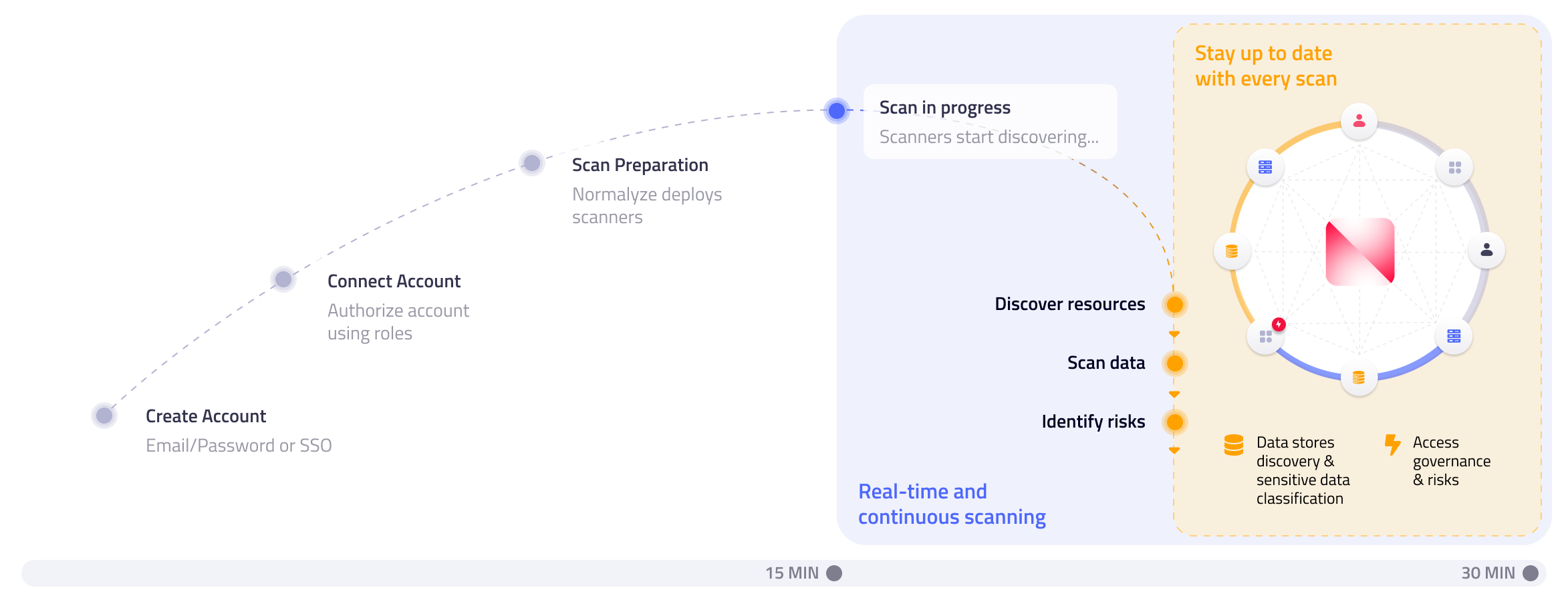
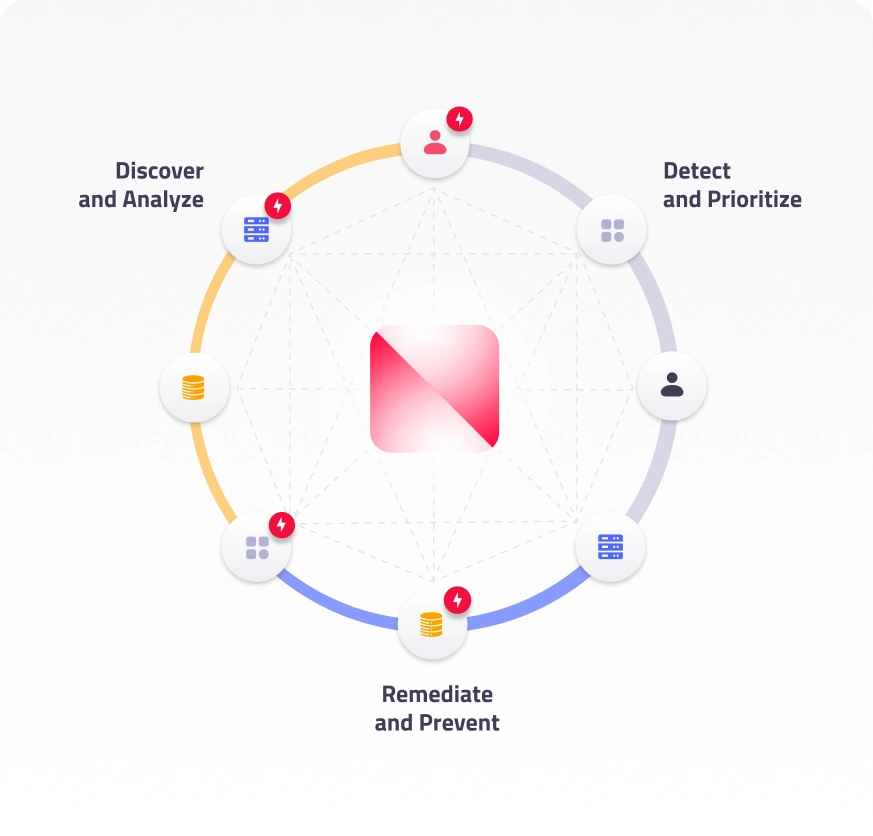
The Normalyze agentless and machine-learning scanning platform continuously discovers sensitive data, resources and access paths across all cloud environments. It generates a graph of access and trust relationships that gives you the ability to analyze, prioritize and respond to cyber threats that can lead to any sensitive data access, and prevent data leakage in real-time.
| Discover and Classify Data |
Normalyze enables rapid and cost-effective discovery and classification of all data stores – even the ones you didn’t know you had – without removing data from your environment. Leveraging advanced algorithms and machine learning techniques, Normalyze enables organizations to gain precise insights into their data landscape with high accuracy in identifying and categorizing data assets.
|
Assess and Prioritize Risks |
Normalyze’s platform uses advanced algorithms, real-time monitoring, and the context of the data to detect and rank potential risks effectively. With a focus on accuracy and timeliness, Normalyze enables organizations to swiftly identify and address data vulnerabilities, ensuring proactive risk mitigation and enhanced data security measures.

Analyze data risk in any environment in two easy steps
|
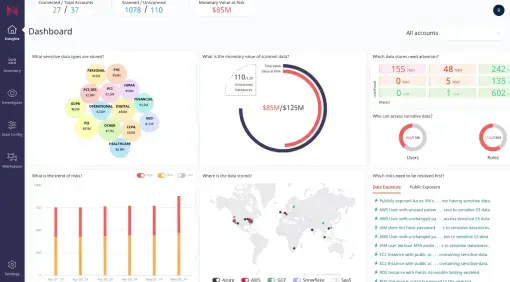
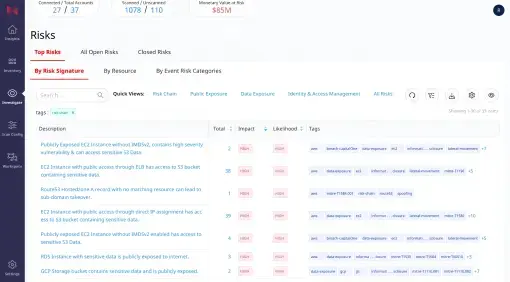
Follow simple steps to onboard all data stores across your hybrid infrastructure into Normalyze. |
|
After viewing dashboards, drill down to assess and remediate the data risks in your hybrid environments. |
Platform Integrations
Normalyze connects to the leading data sources and workflow tools
LLM models
IaaS and PaaS environments
SaaS applications
On-prem environments
Ticketing and collaboration tools
Trusted by
Global Customers

Come work with us
We thrive on innovation, collaboration, transparency and building great tech, while having fun and creating a community around our customers, partners and employees.