All data everywhere
Secure valuable and sensitive data wherever it is for a complete understanding of your data attack surface – all from a single platform.
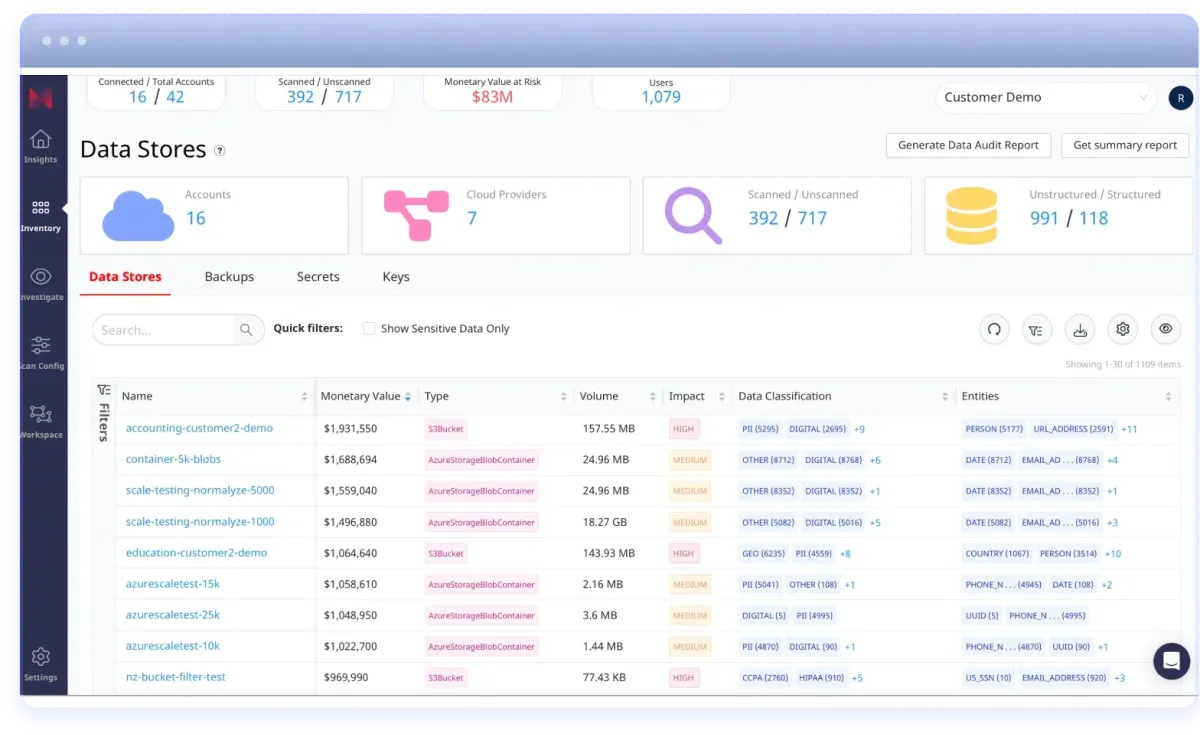
Data security across all environments

Managing data security across hybrid IT infrastructure is an extraordinary challenge in regulatory compliance, data governance, and the prevention of data exfiltration that requires a full range of data protection capabilities applied consistently across the entire infrastructure. Normalyze supports all major SaaS, PaaS, public and multi-cloud, on-premises and hybrid environments, providing consistent, end-to-end visibility and control across your entire data landscape.
- Discover all data, including shadow data and abandoned data, no matter where it resides.
- Classify and validate all data for a complete understanding of your valuable and sensitive data landscape.
- Govern data access privileges against actual usage to identify dormant users and excessive privileges.
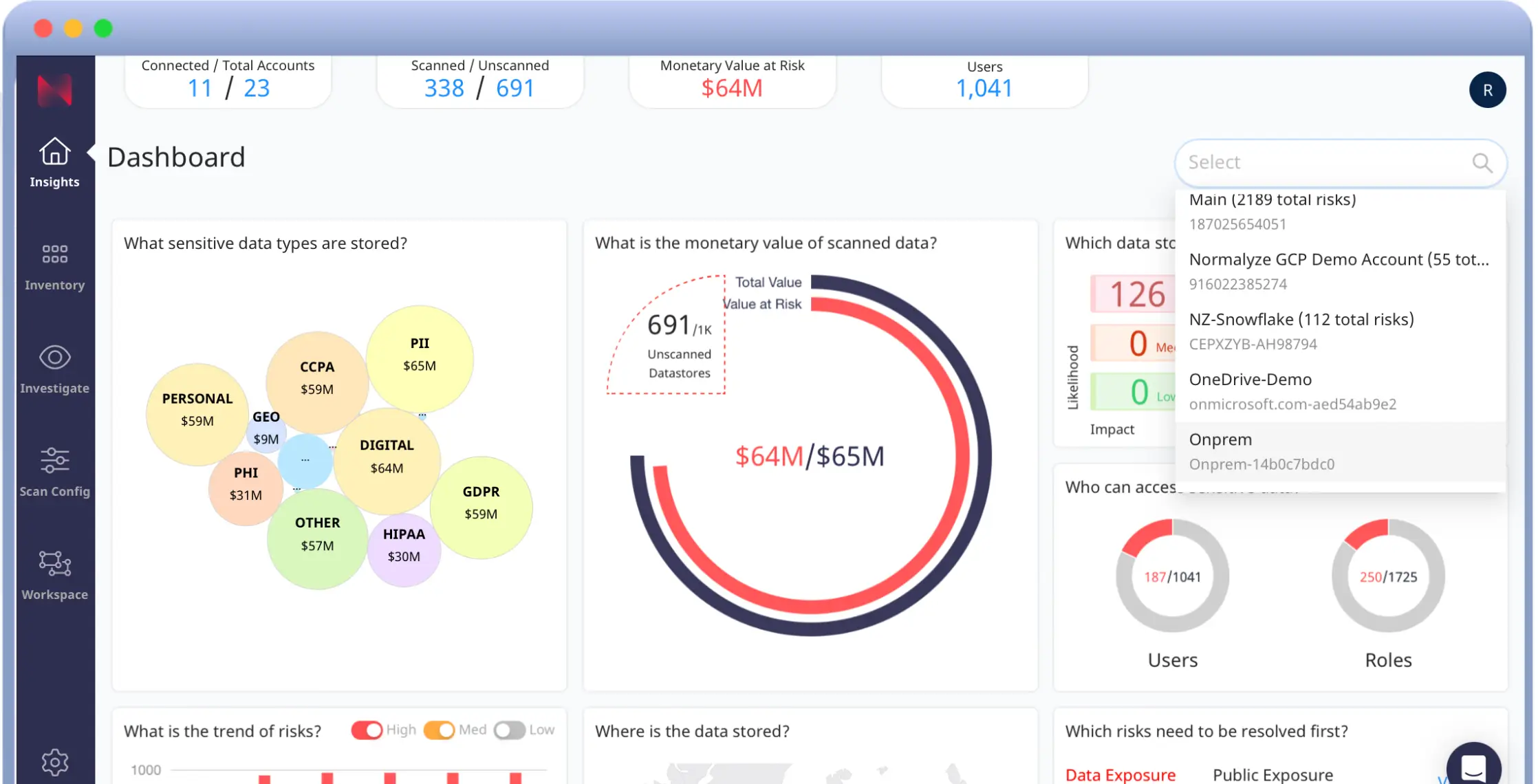
- Identify and prioritize data at risk, so you can kick off effective remediation actions. Continuously monitor for data attack paths and prioritize risky resources, users, or applications with access to valuable and sensitive data
- Save time and money by automating compliance posture, audit reporting, and privacy controls.

LLM models
IaaS and PaaS environments
SaaS applications
On-prem environments
Ticketing and collaboration tools
Infrastucture-as-a-service (IAAS)

With no end in sight to the migration of data to the cloud, it is critical to safeguard valuable and sensitive data in hybrid IaaS environments. The challenge is exacerbated by DevOps processes that automate and accelerate the movement of data and applications to production environments. Normalyze helps alleviate this burden with consistent security capabilities across all major clouds and platforms, including cloud databases and more, giving security teams confidence in discovering all of their valuable and sensitive data and ensuring it is protected.
Platform-as-a -service (PAAS)

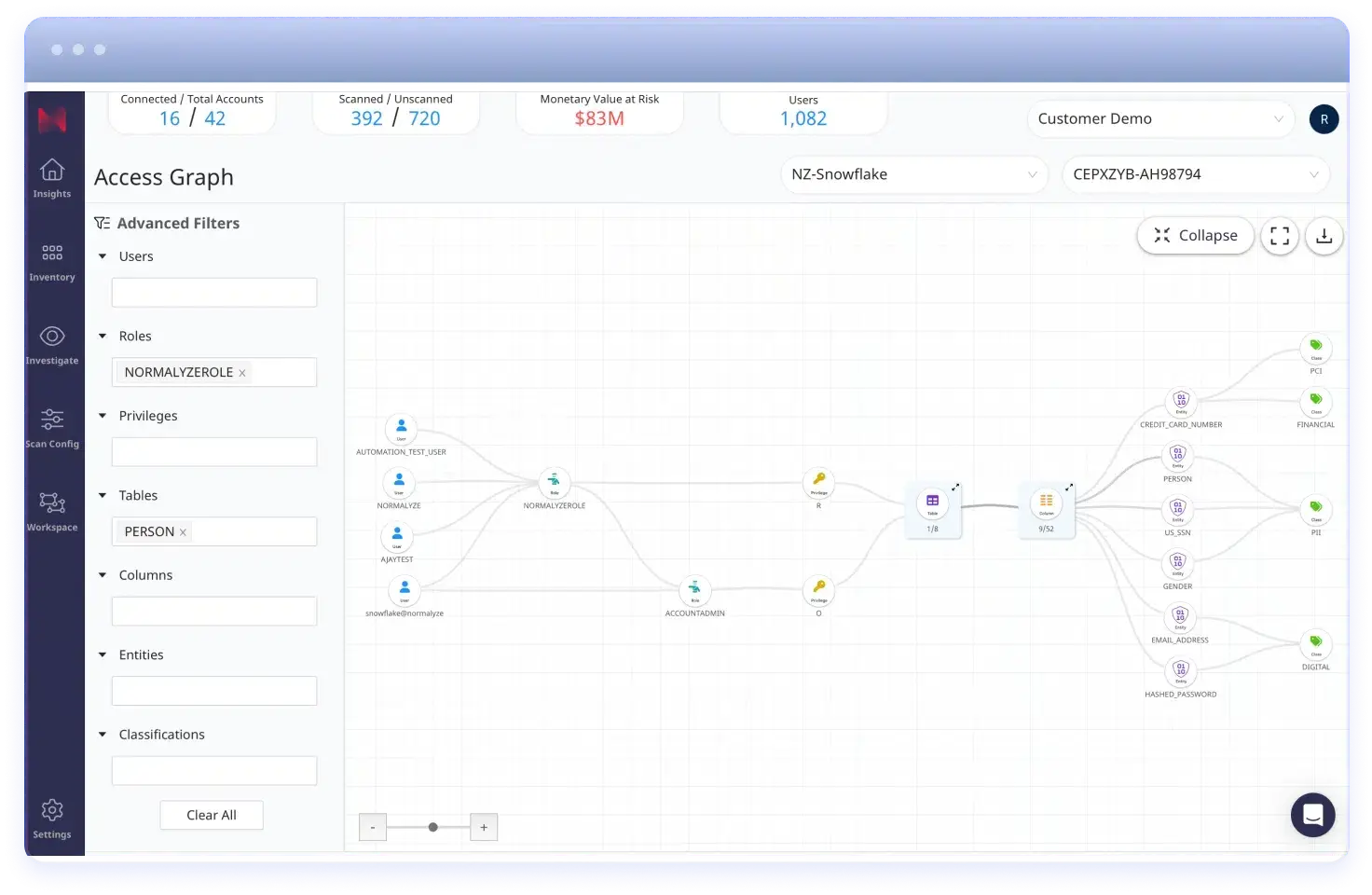
Hybrid PaaS environments tend to involve greater movement of data, more copies of data, and generally more users with access to this data, making the data they contain more difficult for security teams to monitor and control. Normalyze addresses these challenges by building a data catalog with a comprehensive data access graph that shows where valuable and sensitive data resides and who has access to it. This allows security teams to enforce least privilege access to valuable and sensitive data and continuously track and fix potential data risks that can cause data exfiltration and other insider threats.
| Read more about securing Platform as a Service |
Software-as-a-Service (SAAS)
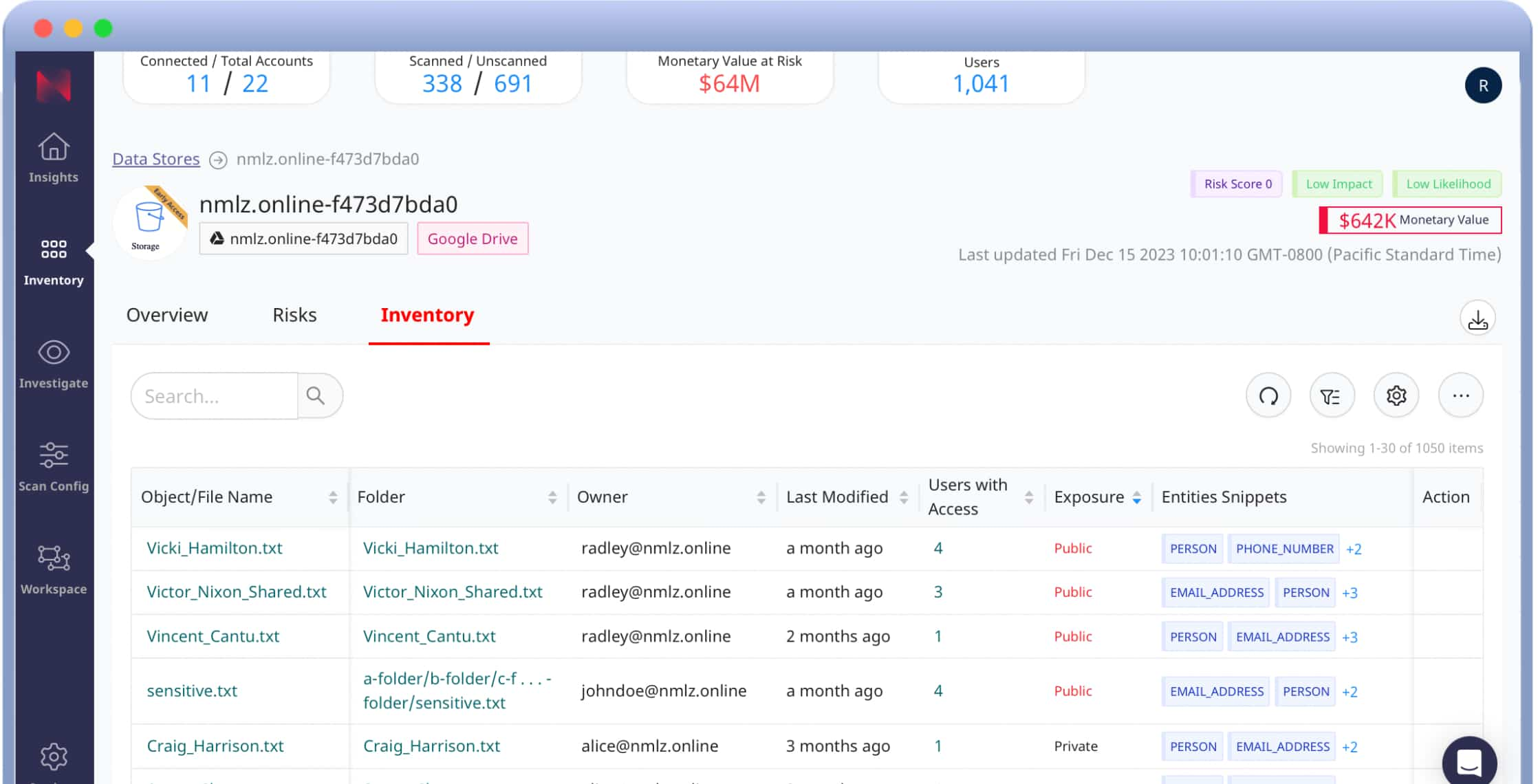
Hybrid SaaS applications often store the largest volume of data within an organization – many organizations run their entire business on apps such as Google Workspace and Microsoft 365. These platforms make it easy to share files, leading to unintended exposure of sensitive data. Normalyze scans and classifies all files and repositories for sensitive or regulated data, mapping out the access and shares to every object, alerting on violations to policy. Ensure least privilege for both internal and external users, alert on behavior anomalies and data exfiltration events. New and modified files are scanned within minutes to provide full and real-time visibility into all data operations.
On-premises data stores
With cost-benefit tradeoffs pushing organizations to keep certain legacy data and applications in their own data centers, on-premises data is not going away anytime soon. Normalyze supports both self-managed as well as cloud-based deployments of scanners to scan on-premises data, including on-premises hybrid databases and network and Windows file shares.
Integrations and
automation
Normalyze provides out-of-the-box integrations with 3rd party ticketing, notification and automation platforms.
This helps security operators to collaborate with DevOps and cloud engineering teams to fix problems in a timely manner and remediate risks.
Out-of-the-box integrations include
visualize, fix
Get a full picture of your valuable and sensitive data landscape and discuss your use case live with a security engineer.