Use cases
Find out how Normalyze helps security and data teams solve some of their biggest challenges.
|
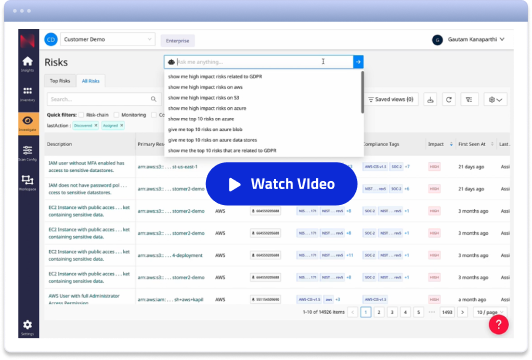
Reduce data access risks Govern data access and enforce least privilege One of the most pervasive challenges security and data teams face is around user access. Without accurately classifying of all of the data they possess, organizations often find themselves in a quandary: balancing the need for access with the imperative of security. When data remains unclassified or is misclassified, it becomes nearly impossible to apply precise access controls. As a result, organizations are forced into a binary choice — either restrict data access to the point of hindering operational efficiency or grant overly broad access, which exponentially increases the risk of data breaches. With automated discovery and classification of all valuable or sensitive data using the Normalyze One-Pass Scanner, including custom data classes and hundreds of other data classes, organizations know at all times what data they have and which of it needs to be protected. With Data Risk Navigator and Data Access Graphs, teams can then review and audit data being accessed at a granular level, map role-based access and privileges, eliminate over-privileged users and adopt the least privilege model, restricting access to the minimum level required.
|
|
Eliminate abandoned data Find stale, duplicate or unknown data sources and minimize attack surface As digital environments continue to expand, the complexity of effectively managing data increases, especially ensuring that all data assets are actively utilized and properly secured. Often, abandoned data is caused by “shadow data” practices or data migration projects. Normalyze’s insights reveal that over 70% of these data stores have been neglected for over a year, and alarmingly, 15% have lingered unattended for three years or more. The implications are twofold: not only do these abandoned data stores lead to escalating storage costs, they also present a severe risk profile, as unmonitored and outdated data can easily become a target for cyber threats. Abandoned data stores should ideally be eliminated or at minimum, offloaded to an archive. Normalyze provides advanced tools specifically designed for identifying and managing abandoned or stale data stores, including backups and snapshots. Our latest update provides detailed insights into the space utilized in backups and the storage tiers used to store them. Since storage costs are proportional to the used size, IT teams can prioritize remediation for the abandoned backups with higher usage. Teams can also get insights on the storage tier—standard or archive — where the backup is stored. |
|
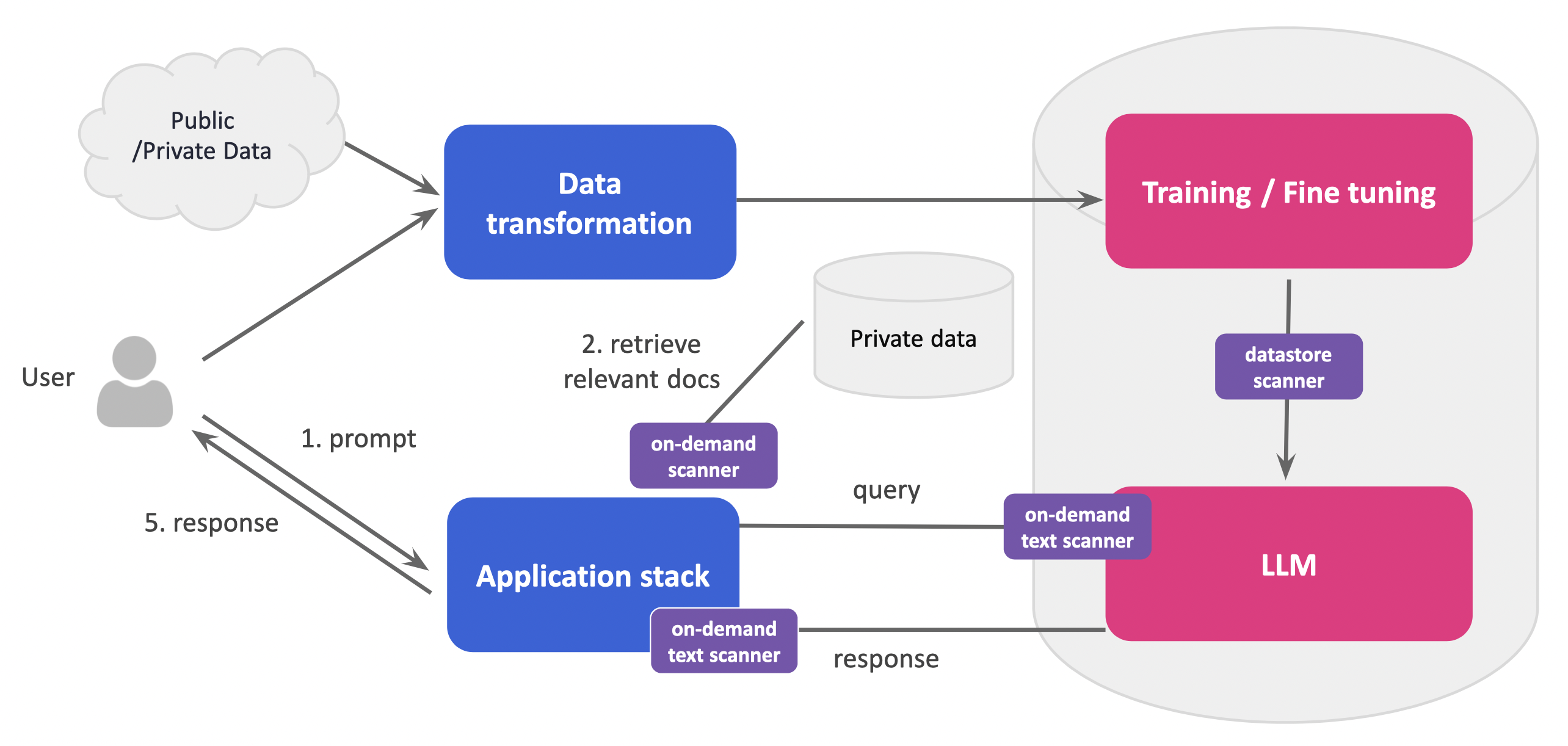
Enable use of AI Leverage DSPM to use Gen AI and Large Language Models confidently Generative AI and Large Language Models (LLMs) are helping enterprises boost productivity, gain competitive advantages and accelerate innovation. These advanced technologies enable the rapid analysis and generation of content, streamlining decision-making and automating tasks. They are also introducing significant data security challenges: without proper data classification, there’s a real risk that these systems might unintentionally process and expose valuable or sensitive information. The challenge is compounded by the proliferation of ‘shadow AI’— technologies deployed directly by business teams without IT oversight. Such deployments can lead to inconsistent security practices and create vulnerabilities, as valuable or sensitive data might be used or accessed in ways that do not align with corporate data governance policies. Normalyze DSPM for AI offers capabilities to scan, identify and classify valuable and sensitive data being used in Large Language Models (LLMs) like Microsoft Copilot or ChatGPT, ensuring that AI-generated content does not expose valuable or sensitive information. In addition, Normalyze also helps secure cloud-based AI deployments in AWS Bedrock and Azure OpenAI by detecting any valuable or sensitive data being fed into the foundational or custom models. Normalyze also offers specialized APIs for LLM security which can be used to conduct real-time sensitivity analysis of data going into and out of LLMs, while providing full governance and visibility into data usage. These APIs can be easily integrated into existing customer workflows, helping keep data processing costs down and increasing security for services like Microsoft Copilot.
|
|
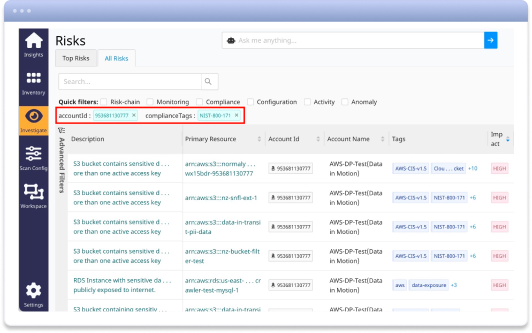
Enforce data governance Continuous compliance with industry regulations and Zero Trust model With data breaches costing companies an average of $4.24 million per incident* and regulatory fines reaching into the billions, organizations must prioritize data security regulations to safeguard their assets and avoid severe financial and reputational damage. The cost of failure to comply with regulations is high (and very public): a multi-national hospitality company was fined $123 million by the UK’s Information Commissioner's Office under GDPR regulations, a financial institution paid an $80 million fine for failing to establish effective risk assessment processes, and a large tech company was fined in excess of $100 million due to failures in their third-party vendor management and data privacy controls. Normalyze streamlines the regulatory compliance process by continuously monitoring and assessing an organization's data security posture against over 500 compliance benchmarks, including NIST 800-171, GDPR, HIPAA, and SOC2. Through automated risk scans, Normalyze identifies compliance gaps and tags violations with specific regulatory frameworks and controls, ensuring teams understand the compliance impacts immediately. Normalyze supports comprehensive remediation by automatically initiating corrective actions through notifications or tickets in tools like JIRA, complemented by AI-generated instructions for efficient resolution. Additionally, Normalyze's compliance reporting features allow organizations to view and report their compliance status across their entire infrastructure, offering detailed views by account, resource, and compliance framework. This enables teams to proactively address vulnerabilities and maintain continuous compliance, effectively preparing them for audits and ensuring ongoing data security. * Source: IBM Security "Cost of a Data Breach Report 2021
|
|
Secure Platform as a Service data Empower the business with the right data and access in PaaS environments PaaS solutions, designed to simplify data management and enhance analytical capabilities, often lead to increased data movement, duplication and complex access structures. Security and data teams often lose control over who accesses what data, raising the risk of data breaches and compliance issues. Normalyze not only simplifies the management of PaaS security but also empowers organizations to maintain stringent data protection standards effortlessly, ensuring that their PaaS environments are both powerful and secure. The patented One-Pass Scanner automates the discovery and cataloging of data across PaaS infrastructures, enabling security teams to track and classify data down to fine details like databases, schemas, and even individual columns. The platform provides a clear, real-time view of data access across the PaaS environment, showing exactly which users have access to valuable and sensitive data and through which roles. This allows security teams to right-size privileges and reduce the risk of overprivileged access. Using tools like QueryBuilder, teams can easily adjust access controls, even if they are not experts in query language. The platform utilizes a library of pre-built risk signatures to monitor and analyze query-level activities continuously, quickly identifying potential security threats such as data exfiltration or insider risks. Real-time alerts for risky activities can be customized to notify teams via popular platforms like email, Slack, Teams, or integrated ticketing systems such as JIRA and ServiceNow, ensuring that any irregular activity is addressed promptly.
|
|
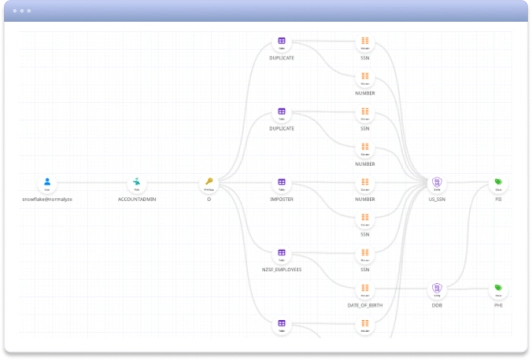
Get DSPM for Snowflake Classify unstructured data to give users access they need without risk. The flexibility of PaaS environments like Snowflake has resulted in greater movement of data, more copies of data, and more users accessing data. While this flexibility is great for data analysts, it causes security teams to more easily lose visibility and control over the valuable and sensitive data in these environments. Using Normalyze’s native integration with the Snowflake AI Data Cloud, customers can now seamlessly secure their data using Snowflake Horizon’s security and compliance capabilities in leveraging the Normalyze patented Data Security Posture Management (DSPM) platform for data discovery, classification, access governance, risk management, and compliance. Leverage Normalyze Data Access Graphs and Normalyze Risk Navigator to view the top risks against your Snowflake data, filterable by tags and sortable by impact and likelihood. Click the risk to find each instance of that risk and detailed remediation instructions. Implement best practices like least privilege enforcement and multi-factor authentication for admin users with access to valuable and sensitive data. Deploy anomaly detection to track data access patterns and spot credential abuse.
|
Trusted by
global customers
What creates data security challenges?

Abandoned data
Misclassified Data
Overprivileged Access
False Results During Audits
Unenforceable Data Policies
Shadow Data
AI-Generated Content
Complex Data Environments
Data Velocity and Volume
Regulatory Changes