It’s necessary to implement robust data security services to limit unauthorized access to sensitive data while still preserving ease of access for those with legitimate needs. Learn below how to prevent the leakage of confidential information in the cloud.
What Is Data Leakage?
A data breach happens when private or protected data is accidentally or deliberately exposed without authorization. This typically involves the unauthorized revelation of sensitive information like client details, personal contact numbers, medical records, financial data, social security IDs, and credit card numbers.
In 2023, the average cost of a data breach was 4.45 million U.S. dollars. As such, data leakage is a significant threat to healthcare, retail, financial, and numerous other organizations as they aim to protect sensitive data and remain in compliance.
How Do Data Leaks Happen?
Data breaches occur for various reasons. They may stem from a cyberattack that breaches the organization’s defenses or inadequate security and visibility measures within its data.
Human mistakes are common causes. Additionally, breaches can result from the actions of disgruntled employees or insiders with harmful intentions.
But, in most cases, data leakage occurs primarily from insufficient security awareness, subpar security protocols, and system misconfigurations. Ultimately, it’s the gaps in the data security posture that allow for data exposure in the first place.
How Can You Prevent Data Leakage?
The best defenses against data leakage are based on principles of security and visibility. Here are three simple steps to find, classify, and restrict access to sensitive data:
1. Data discovery: Create a comprehensive catalog of identities (users, resources, and their roles), data stores, and compute resources present in all your cloud accounts, presented in a detailed graph that allows you to view them collectively with precision.
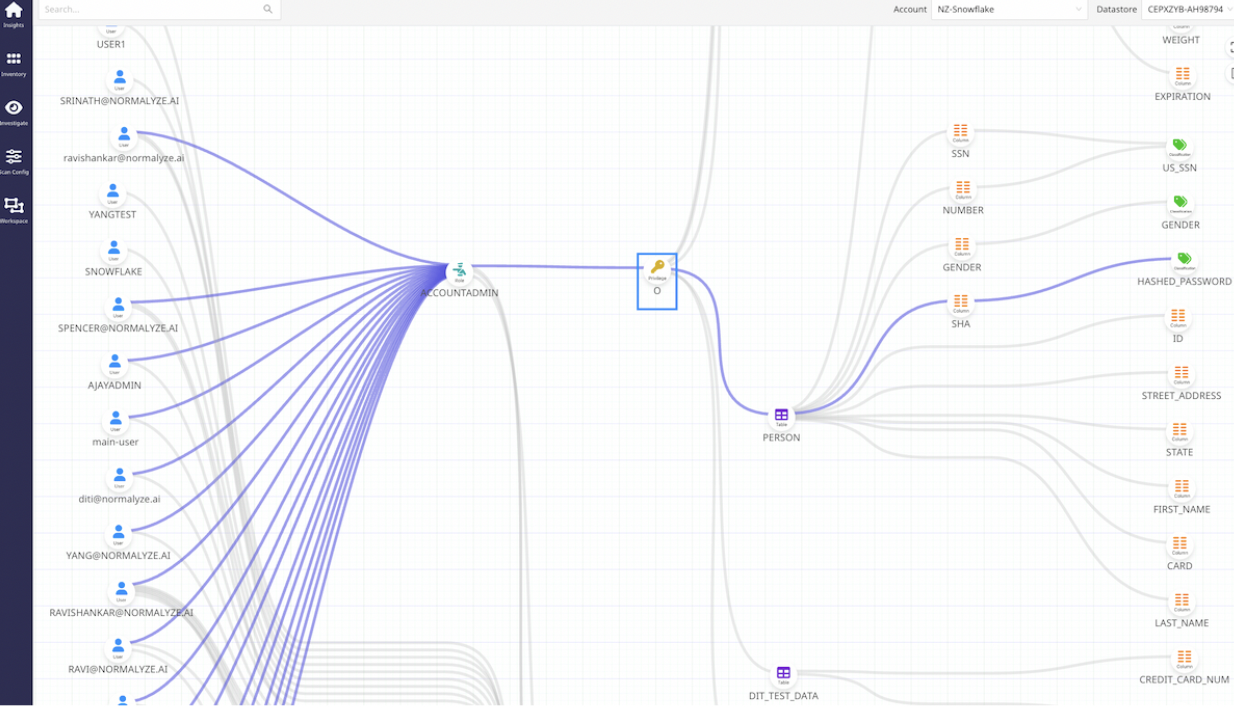
2. Review access: Perform ongoing audits of access and privileges linked to data stores and various cloud resources. The key is that it is automated.
3. Enforce least privilege access: Revoke access from individuals who no longer require or utilize it, ensuring that users only possess access to the essential resources and data required for their role.
How Does A Data Leakage Prevention Tool Work?
Organizations need a deep understanding of their data security posture to secure confidential information in the cloud effectively. While ensuring comprehensive security is necessary, IT staff should have limited access to sensitive materials. Organizations must maintain privacy and data integrity and should restrict access to authorized personnel only. Implementing access controls, permissions, and user authentication mechanisms are essential to preventing unauthorized data leakage of confidential information.
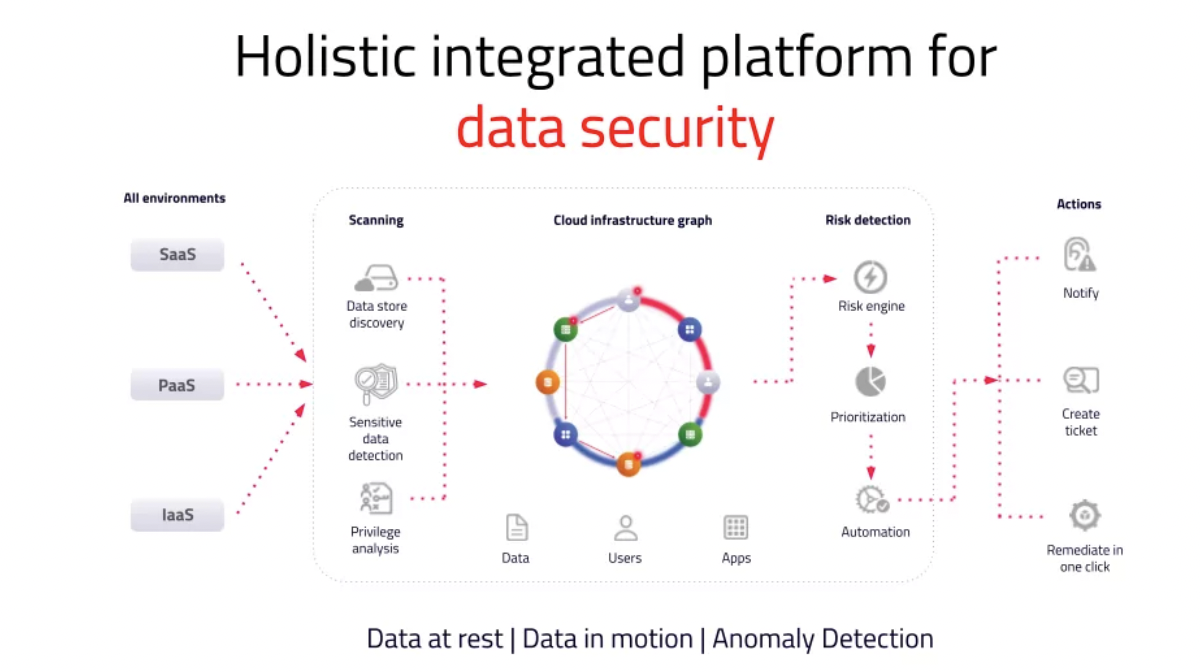
A data security posture management tool like Normalyze Normalyze’s data security posture management (DSPM) solution provides comprehensive insights into data security posture while continuously discovering and fixing the risks of cloud data in motion and at rest within one unified platform.
Balancing Cloud Data Security and Accessibility
The Challenges of Cloud Data Protection
Hosting sensitive data in the cloud introduces complexities that organizations must address to ensure data security.
- Continuous Integration and Continuous Deployment (CI/CD) leads to a proliferation of deployments and frequent updates, resulting in an increased likelihood of software bugs and potential cloud data breaches. This is due to the rapid and continuous nature of the service delivery, which leaves little room for manual review and validation.
- As data scientists experiment with AI/ML models and evolve them for new business requirements, new data stores are created for testing and training. This constant movement of production data into nonproduction environments may expose it to potential leakage.
- Modern app development uses multiple microservices with their own data stores containing overlapping application data. This complicates securing data, especially as new features often introduce new microservices with more data stores.
- The proliferation of copies of data in different cloud storage locations (AWS, Azure, GCP, and Snowflake) is a big issue for organizations using infrastructure as a service (IaaS) and infrastructure as code (IaC) options. These architectures allow getting things done quickly, but “faster” often means there’s no one looking over your shoulder to apply security checks to the expanding data.
- Reliance on cloud infrastructure becomes a security challenge when data access is misconfigured. According to Gartner analysts, most cloud data breaches are due to the misconfiguration of cloud infrastructure, especially IaaS and PaaS.
- Data subject to privacy regulations such as personally identifiable (PII) data for GDPR, payment account data and sensitive authentication data for PCI DSS, and personal health data for HIPAA require more control and tracking. Noncompliance in protecting sensitive data like these can trigger substantial penalties and a significant risk of leakage of confidential information in the cloud.
Additional challenges include maintaining extensive insight into data security posture, restricting access to sensitive materials, and preventing unauthorized data leakage or breaches.
Achieving Cloud Data Visibility and Access Governance
With Normalyze, organizations balance security and accessibility, safeguarding their confidential information in the cloud. What sets Normalyze’s DSPM services apart from the rest?
- Monetary value assessment of data stores
- Automation for creating custom rules and driving automated actions on risks
- Extensive customization to suit the unique needs of every enterprise, including custom entities, profiles, and risk signatures
- Patented data attack path detection to identify the risk of a data breach
- Patented one-pass scanner for cost-efficient scanning
These unique features set Normalyze apart from other data security posture management solutions, allowing organizations to prioritize their security efforts, automate risk mitigation, customize the solution to their specific needs, assess the risk of a cloud data breach, and conduct thorough scanning while optimizing costs. Normalyze empowers businesses to enhance cloud data security and protect their valuable data assets.
