Data Risk Management
Is your data at risk of a breach?
 RISK IDENTIFICATION
RISK IDENTIFICATION
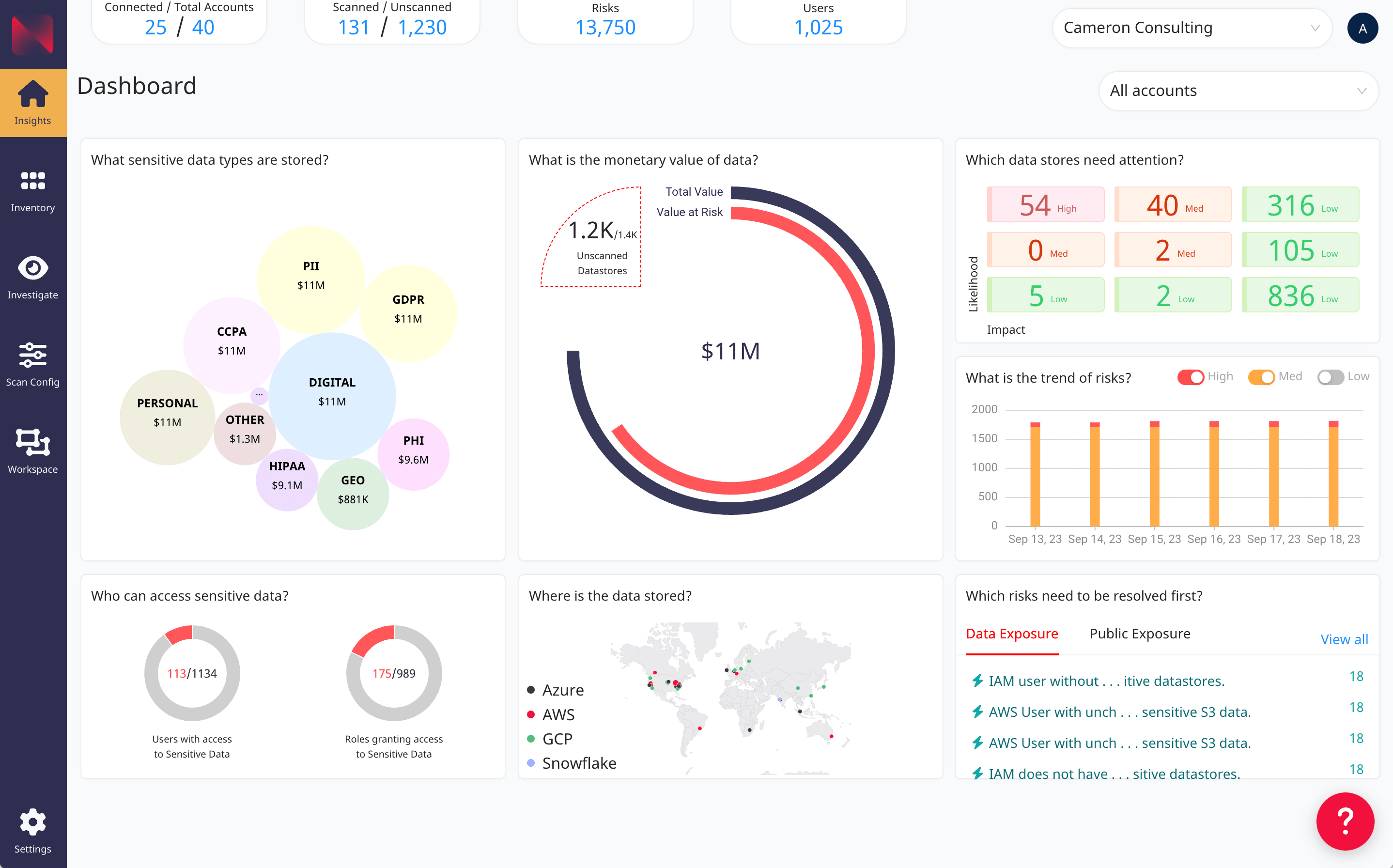
Automatically identify risks to your cloud and on-prem sensitive data, including public exposure, excessive data permissions, data exfiltration, and anomalous user activity. Visualize your security risk posture in real time with a graph of access and trust relationships that includes deep context with fine-grained process names, data store fingerprints, cloud IAM roles and policies. Using patented technology, Normalyze goes a step further to determine potential attack paths by tracing network paths at scale between cloud-resident sensitive data and all points of access.
 Normalyze puts the spotlight on risk:
Normalyze puts the spotlight on risk:
- Continuous monitoring across hybrid & on-prem
- Visual graph of access and trust relationships
- Identity and access management risk assessments
- Awareness of data context
- Anomalous activity detection
- Patented attack path detection
 RISK PRIORITIZATION
RISK PRIORITIZATION
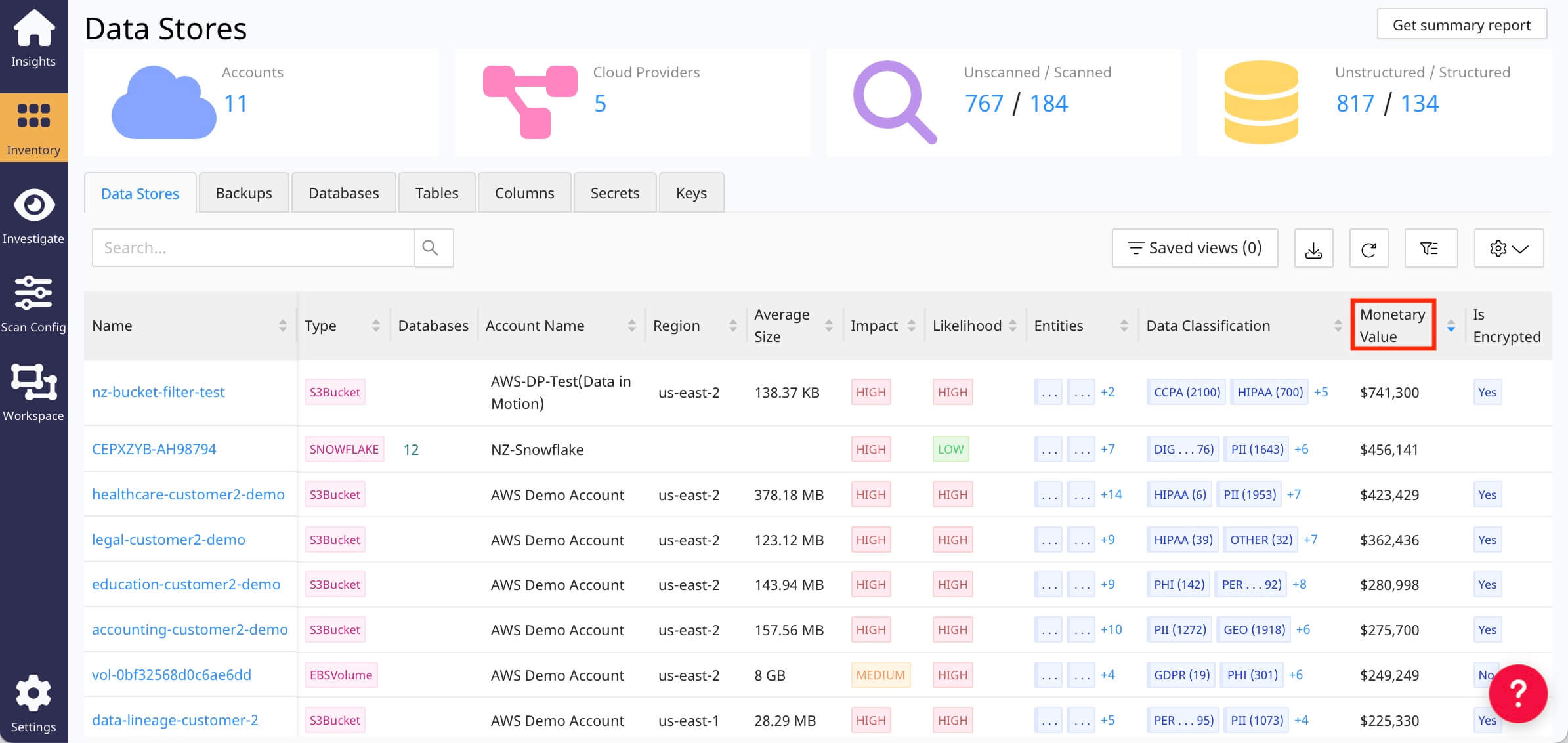
The monetary value of your data gives a quantitative metric to assess, communicate, and prioritize overall data security risk based on the cost of a potential breach. Rich risk scoring based on sensitivity, volume, and permissions allows security teams to advise stakeholders on the potential business impact of unaddressed risks.
Normalyze automatically calculates the monetary value of your data based on the historical cost-to-handle per breached record of equivalent data.
Drill into the high-value data stores to find the priority risks that need to be resolved first.
 REMEDIATION
REMEDIATION
Out-of-the-box integrations with third-party ticketing, notification and automation platforms help security operators collaborate with DevOps and platform engineering teams to remediate risks in a timely manner. Detailed, AI-generated instructions take the burden of research off remediation teams by showing how to remediate each issue. Automated remediation workflows ensure continuous safety and compliance of sensitive data.
DATA RISK MANAGEMENT IN ACTION
Monetary Value Paints the Big Picture
Get a personalized demo of Normalyze
Our security engineers will demonstrate the data compliance, discovery, classification, risk prioritization, and remediation capabilities of the platform. The live demo format lets you ask questions that are relevant to your business and security environment and requirements.