How to Get Started, Key Components, and Common Mistakes
Data security is paramount in today’s digital landscape, especially with the increasing reliance on cloud infrastructure. Incorporating Data Security Posture Management (DSPM) tools into your cloud data security solutions will help safeguard your organization’s most valuable asset – data. This blog post provides insights, tips, and answers to frequently asked questions about DSPM solutions.
How to Succeed with (DSPM) Tools:
- Understand Your Data: Begin by gaining a clear understanding of your data landscape, including the locations of structured, unstructured, and shadow data stores, abandoned databases, and sensitive data types across SaaS, PaaS, public or multi-cloud, on-prem and hybrid environments. Conduct thorough data discovery and classification.
- Evaluate Access Governance: Evaluate who can access your data and identify excessive privileges. Implement robust access controls and regularly review and update user permissions to minimize the risk of unauthorized access.
- Implement Risk Management Measures: Develop a comprehensive risk management strategy to identify, prioritize, and mitigate potential data breach risks. Continuously monitor and assess your data security posture to address vulnerabilities proactively.
Key Components of Data Security Posture Management:
- Data Discovery and Classification: Automatically discover and classify data across your cloud infrastructure, identifying its location, sensitivity, and associated risks.
- Access Governance: Control and manage data access, ensuring appropriate permissions and minimizing the risk of unauthorized access.
- Risk Management: Identify, assess, and prioritize potential risks to your data, implement measures to mitigate those risks, and maintain a strong security posture.
- Compliance: Ensure adherence to relevant regulations, such as PCI and GDPR, by implementing necessary controls and processes.
Common Mistakes with Data Security Posture Management:
- Inadequate Data Visibility: Failing to comprehensively understand data locations, types, and associated risks can leave organizations vulnerable to data breaches.
- Singular Focus on Discovery and Classification: Merely concentrating on data discovery and classification is insufficient for effective risk prioritization. To truly prioritize security measures, organizations must delve deeper into:
- Assessing the business impact and monetary value associated with each data asset.
- Evaluating the risk of a data breach or compromise.
- Poor Access Controls: Neglecting to establish proper access controls and reviewing user permissions can result in excessive privileges and unauthorized data access.
- Lack of Continuous Monitoring: You need to monitor and assess the security posture of your data continuously to ensure you are aware of potential vulnerabilities or changes that could impact data security.
- Lack of Scale: Data volumes are exploding, especially when the business wants to leverage Large Language Models or data lakes or undertake major data initiatives.
- Ignoring Compliance Requirements: Neglecting to comply with relevant data protection regulations can lead to legal and reputational consequences.
- Incomplete Risk Detection: Relying solely on data store configuration for risk detection provides an incomplete picture of data security risks. It is essential to go beyond configuration and analyze the context of the data you are protecting:
-
- Identifying risky resources/users with access to sensitive data.
- Monitoring and analyzing actual data activity surrounding the datastore.
- Detecting anomalies and unknown risks that may evade standard security protocols.
An Ongoing Process
Incorporating Data Security Posture Management (DSPM) tools into your data security strategy is essential for effectively protecting your organization’s valuable data. By following the tips outlined in this post and understanding the critical components of DSPM, you can establish a robust data security posture and minimize the risk of data breaches. Avoiding common mistakes will further enhance your data security efforts, ensuring your data assets’ confidentiality, integrity, and availability.
Furthermore, a core element of the evaluation of DSPM solutions is weighing the various technical features against the organization’s requirements. This Buyers’ Guide lists technical capabilities that should be confirmed in each DSPM solution during evaluation.
Remember, DSPM is an ongoing process that requires continuous monitoring, assessment, and adaptation to evolving threats and regulatory requirements. Stay proactive and prioritize data security to safeguard your organization’s sensitive information.
What Sets Normalyze Apart From the Rest?
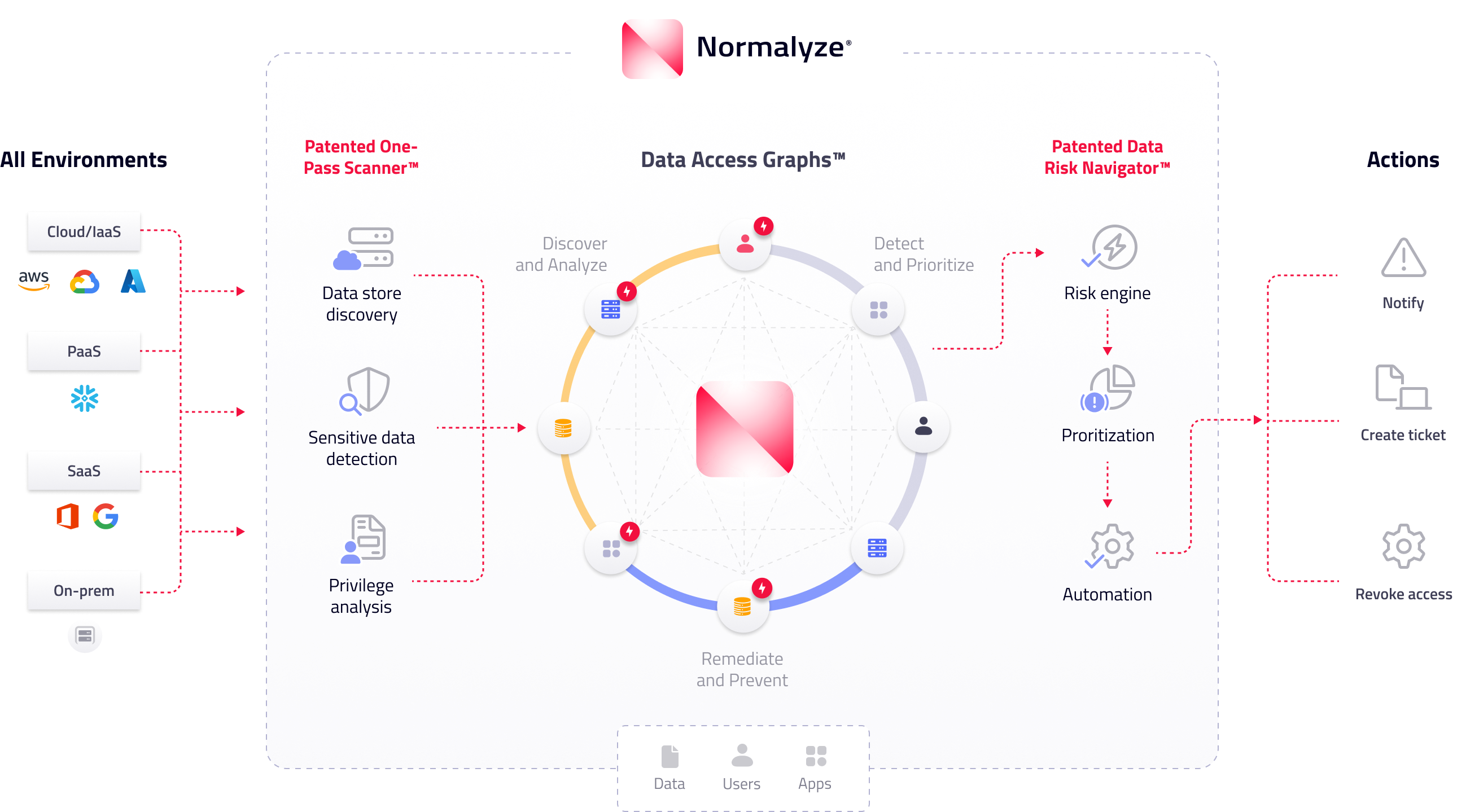
-
- Patented One-Pass Scanner for cost-efficient scanning
- Data Access Graphs to highlight which users and resources have access to sensitive data
- Patented Data Risk Navigator to visualize attack paths that could lead to data breach or loss
- DataValuator to assess the relative business impact of potential data loss
- DSPM for AI to prevent AI-generated content from using unauthorized data
- DSPM for Snowflake to scan massive amounts of data and manage access
- Automation for creating custom rules and driving automated actions on risks
- Extensive customization to suit unique needs of every enterprise, including custom entities, profiles, and risk signatures
These unique features set Normalyze apart from other Data Security Posture Management solutions, allowing organizations to prioritize their security efforts, automate risk mitigation, customize the solution to their specific needs, assess the risk of a breach, and conduct thorough scanning while optimizing costs. Normalyze empowers businesses to effectively enhance their data security posture and protect their valuable data assets.
See Normalyze’s DSPM Tools for Yourself
See Normalyze in action. Request a demo or take advantage of our Data Risk Assessment to understand how our platform can make a significant difference in managing and securing your organization’s most valuable data assets.

