New features
history archive
Get the most current releases, features and capabilities
in the Normalyze platform.
See the newest Normalyze features
Advanced Data Governance and Consumption Cost Management
As data volumes grow and more applications and users access data, Normalyze is helping customers reduce their overall data consumption costs while making sure compliance requirements are being met.
-
Improved Coverage of Redundant and Obsolete Data (ROT): Enhanced algorithms now identify and manage redundant, obsolete, and trivial (ROT) data at scale, helping reduce storage costs and improve data hygiene.
-
Duplicate and Redundant Data Detection: Tools to identify and manage duplicate data, optimizing storage and reducing costs.
-
Obsolete Data Algorithms: Algorithms to detect obsolete data based on age or access frequency, further refining our data governance capabilities.
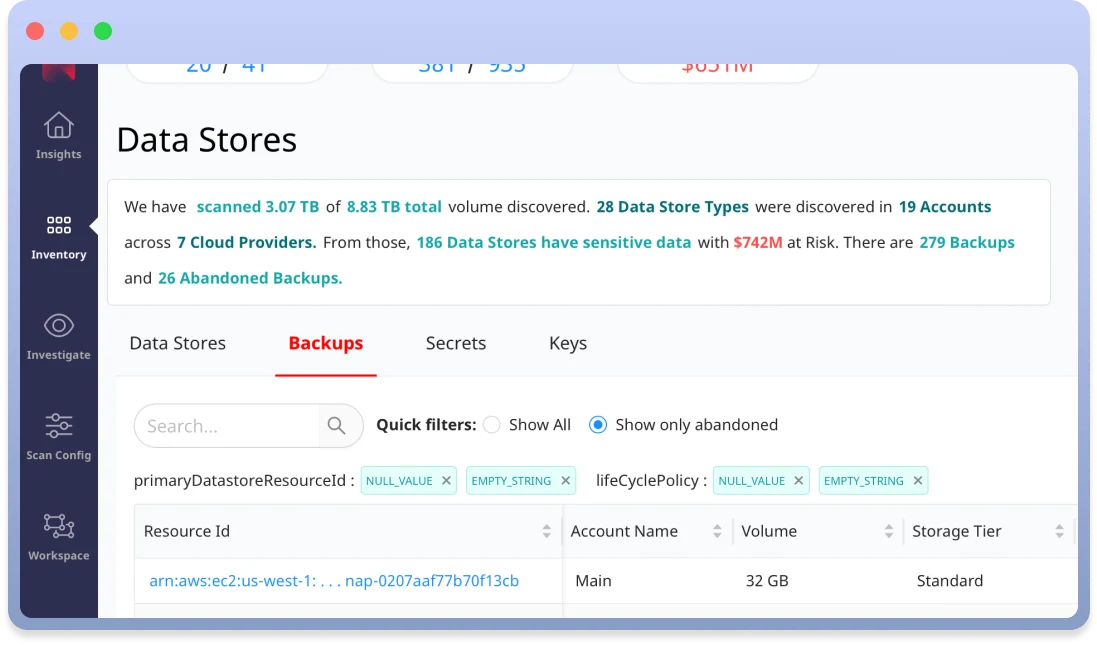
- Deeper GCP Coverage: Added context on Google Cloud Platform data, including last accessed timestamps, detailed IAM entity information, organization onboarding, and discovery of GCP backups.
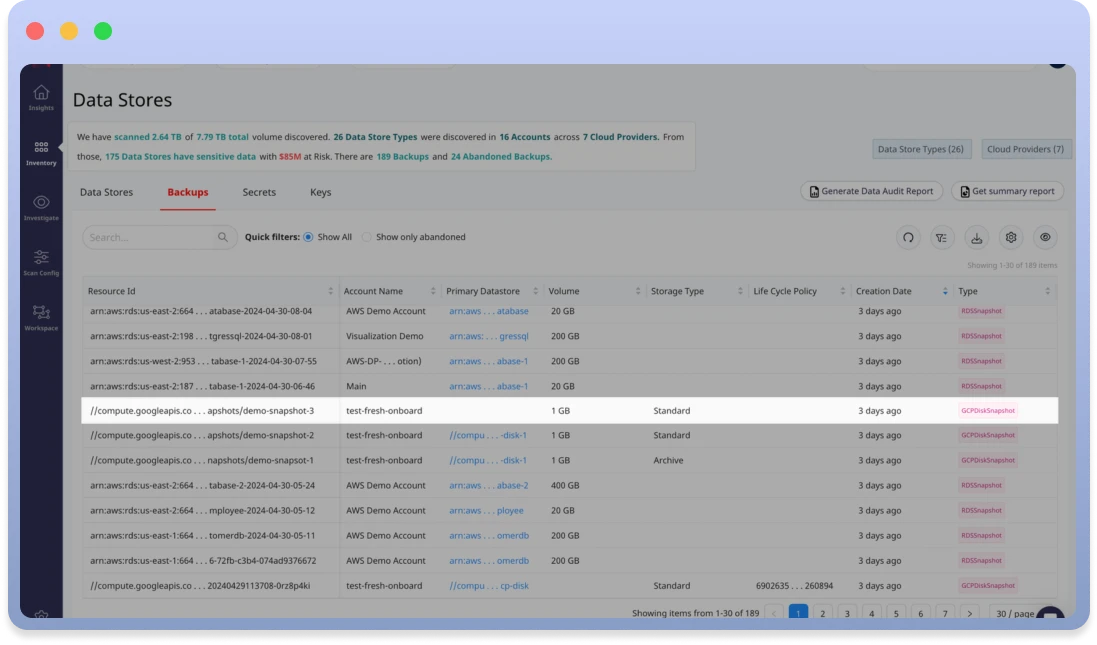
Abandoned Data Explorer™
Normalyze’s insights reveal that over 70% of data backups have been neglected for over a year, and alarmingly, 15% have lingered unattended for three years or more. Not only do these abandoned data stores lead to escalating storage costs, but they also present a severe risk profile, as unmonitored and outdated data can easily become a target for cyber threats.
The Abandoned Data Explorer™ enables teams identify and manage abandoned or stale data stores, including backups and snapshots. Get detailed insights into the space used in your backups and the storage tiers used to store them, so you can prioritize remediation for the abandoned backups with highest usage. A customer reported finding abandoned data that was costing them nearly $18k a month to store.
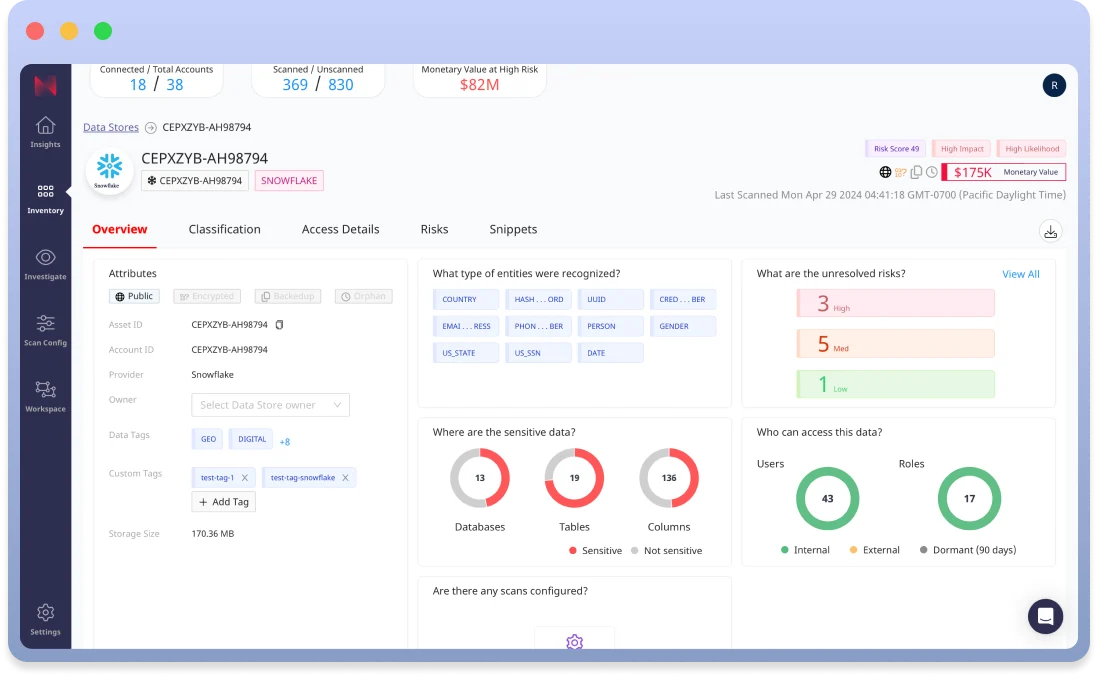
Snowflake Native App for DSPM
Snowflake customers can now apply advanced tools for automated data discovery and classification at big data scale, precise access management and least privilege enforcement, and proactive risk monitoring with anomaly detection to enhance their security measures across their Snowflake data landscape and ensure compliance with regulatory requirements.
Using Normalyze’s native integration with the Snowflake AI Data Cloud, customers can now seamlessly secure their data using Snowflake Horizon’s security and compliance capabilities in conjunction with the Normalyze patented Data Security Posture Management (DSPM) platform for data discovery, classification, access governance, risk management, and compliance.
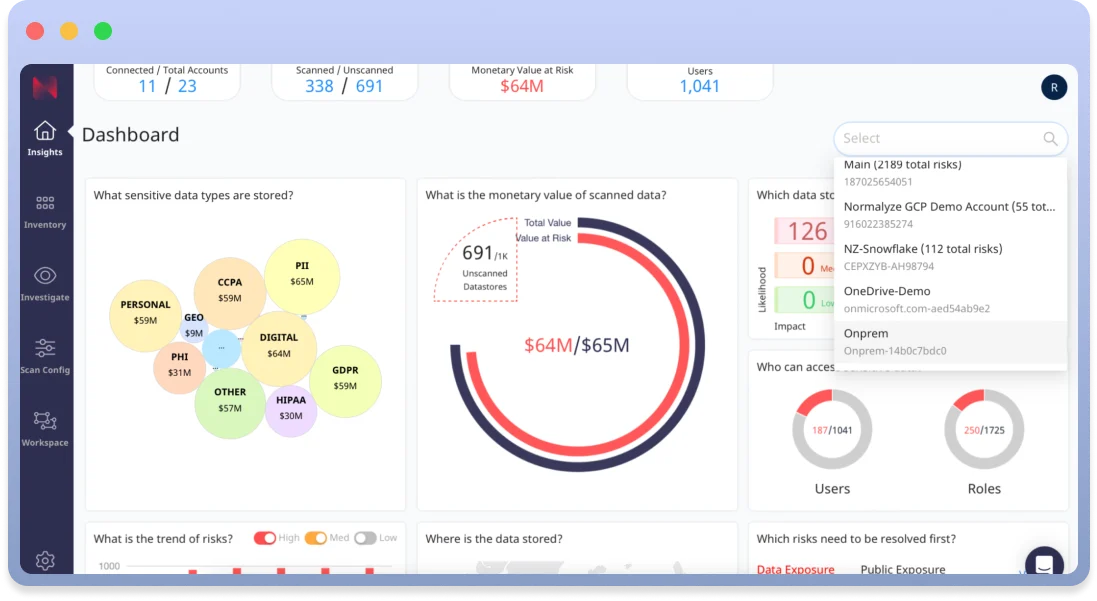
Expanded DSPM for On-Premises
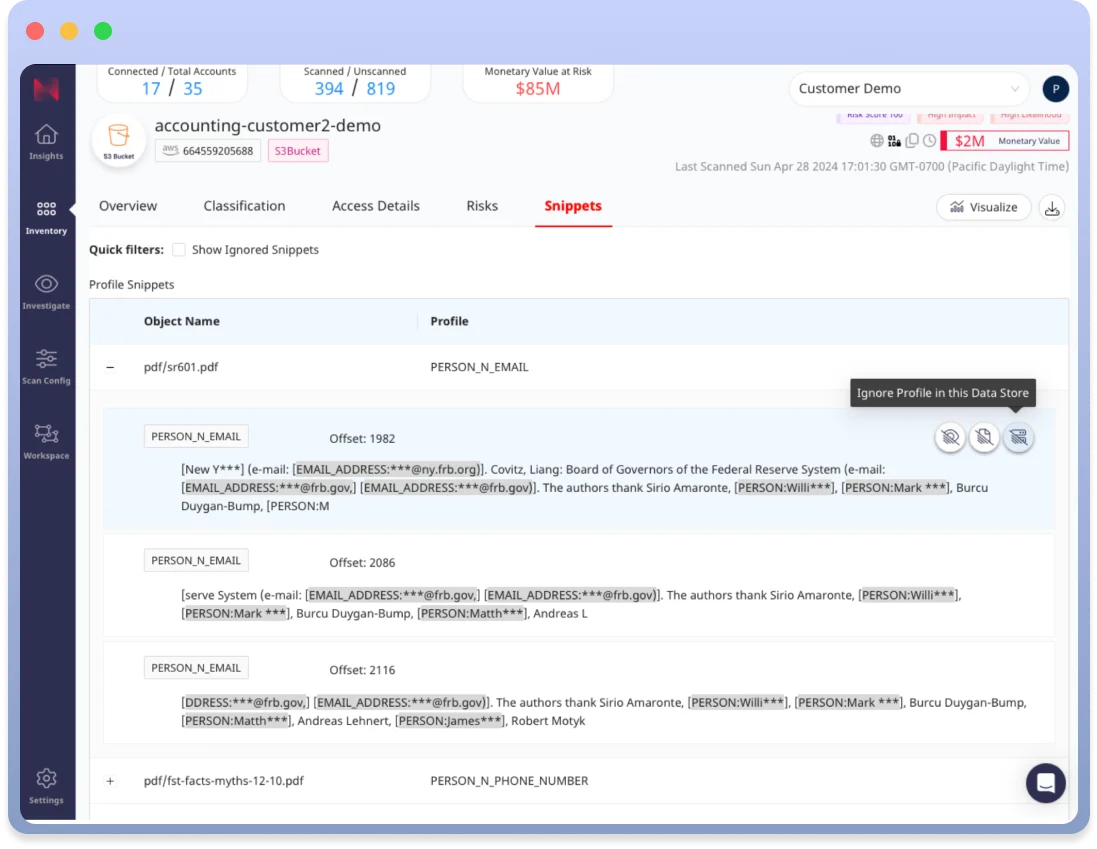
New Workflows to Validate Classification and Sensitive Data
New Validation Workflows give finer control to manage and optimize data security operations, with the capability to validate data classifications and entities at a granular level—either object or snippet—that directly impact the alerts and dashboards.
Prioritize Critical Security Risks and Data: Through Normalyze’s Validation Workflows, teams can target scanning and classification on specific, high-priority data elements at the object or snippet level, ensuring focus on genuine threats and reducing non-critical alerts. That means you can target scanning on known high-importance data and ignore known low-risk data, thereby reducing alert noise and improving operational efficiency.
Tailor Protection to Fit Organizational Needs: These workflows empower teams to customize how data is classified and flagged within the platform, adjusting alert sensitivity and specificity according to the unique needs and priorities of the organization. By fine-tuning how data is handled at the snippet or object level, teams can ensure that the most relevant and significant data points are highlighted in security alerts and dashboards, streamlining investigations and ensuring that security measures are directly aligned with organizational strategies.
visualize, fix
Get a full picture of your sensitive data landscape and discuss your use case live with a security engineer.