Data Security and Protection
for All Critical Data
The Cohesity-Normalyze Integration delivers best-of-breed Data Security Posture Management (DSPM) with cyber recovery and ransomware protection for all data across cloud, SaaS, and on-premises environments.
Safeguard What Matters Most – Your Data
The joint solution enables more efficient identification of sensitive data to provide automatic protection, recovery, and defense against detected data risks that can lead to expensive data breaches and ransomware.
The joint solution enables more efficient identification of sensitive data to provide automatic protection, recovery, and defense against detected data risks that can lead to expensive data breaches and ransomware.
1 |
Discover |
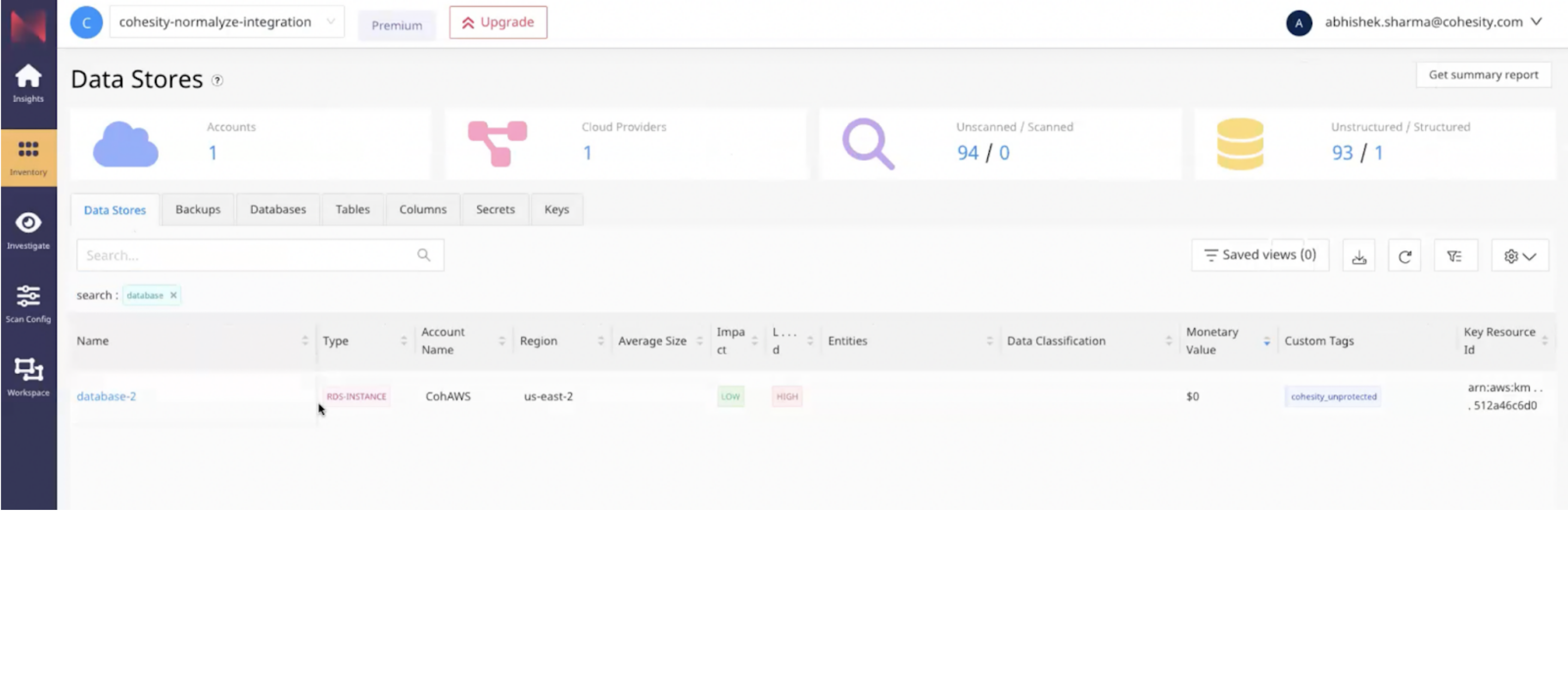
| Continuously discover all datastores and cloud resources across multi-cloud, SaaS, and hybrid environments. In Normalyze, customers will see status of Cohesity protection in the form of custom tags. |
2 |
Identify Sensitive Data |
| Perform sensitive data classification in over 30 data stores across multiple cloud platforms and on-premises environments in minutes. |
3 |
Prioritize Risks |
| Prioritize risk remediation based on the monetary value associated with the loss of sensitive data in the event of a breach. |
4 |
Find attack paths |
| Understand the level of risk around critical data and the attack paths that lead to the compromise of sensitive data with detailed remediation steps and workflows to fix it. |
5 |
Protect and recover |
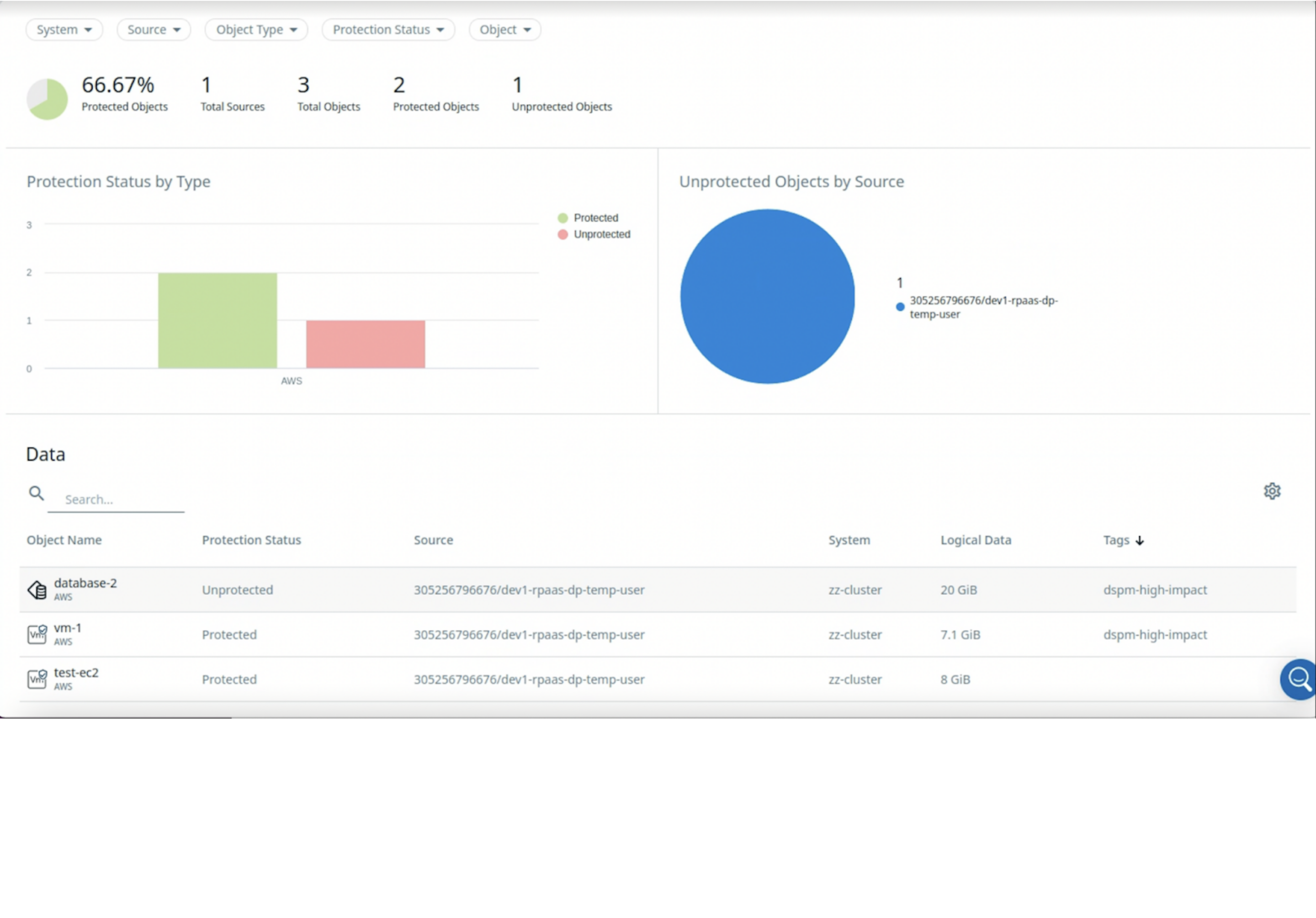
| Automatically close the loop around data risks and mitigate them with Cohesity’s data protection and data recovery solution. In Cohesity, at-risk data stores are marked as high impact by Normalyze. |
Data Security at Scale
The integrated solution provides organizations with a comprehensive approach to data protection at scale following the fundamentals of the NIST Cybersecurity Framework.

Identify
Discover, classify and contextualize the data
Protect
Minimize access to sensitive data or protect data through encryption, masking, or anonymization
Detect
Monitor every data access and alert on abnormal behaviors such as excessive data movements or data proliferation
Respond
Understand the blast radius of a compromise and what data was compromised to communicate quickly and facilitate remediation or mitigation
Recover
Make the data available again by cleaning the malware and recovering clean data
Trusted by
Global Customers
DEMO
Cohesity &
Normalyze demo
Our security engineers will demonstrate the data protection, recovery, and defense against costly risks capabilities of the integrated solution. The live demo format lets you ask questions that are relevant to your business and data security requirements.