LastPass disclosed technical details of a second breach, with major implications for critical datastores, including encrypted and unencrypted customer data in the LastPass production AWS S3 buckets.
The new incident
The new attack was a lateral move leveraging information captured during the first breach last August. The new target was a senior DevOps engineer whose personal home computer was compromised with an installed keylogger. Captured data allowed the attacker to access the engineer’s corporate vault, which contained encrypted notes with LastPass production cloud environment access details. The notes may have contained access keys, private decryption keys, and other sensitive information that allowed the attacker to gain access and exfiltrate and decrypt customer data stored in LastPass AWS accounts.
Lessons learned from the breaches
The LastPass incident highlights severe consequences of a cyber breach of highly-sensitive individual and corporate user data. Observers question the sufficiency and effectiveness of security measures established to safeguard cloud-stored critical data. Based on the incident summary reported by LastPass, we learn three lessons that organizations can use to improve their cloud data security posture.
1. Better data access governance of privileged IAM users
The primary vulnerability was access to and use of a privileged user’s credentials for breaking into LastPass production cloud accounts. Attack vectors like these are difficult to detect and monitor proactively. LastPass was unable to detect unauthorized access because the attacker used proper credentials.
The company’s investigation found the original breach and data theft occurred between August 12th to October 26th, 2022. A company statement on December 22, 2022 addressed security process changes, such as the rotation of compromised credentials. This suggests previously insufficient or unenforced measures were used to rotate long-term access credentials within standard timeframes of 60 or 90 days, particularly credentials for direct access to highly-sensitive data. Cloud providers recommend the rotation practice as part of a shared-responsibility model, and not adhering to it could potentially violate LastPass compliance requirements. Also, the principle of least privilege may not have been applied to the breached engineer’s access rights. A better approach would have been an Assume Role-based architecture to access cloud resources.
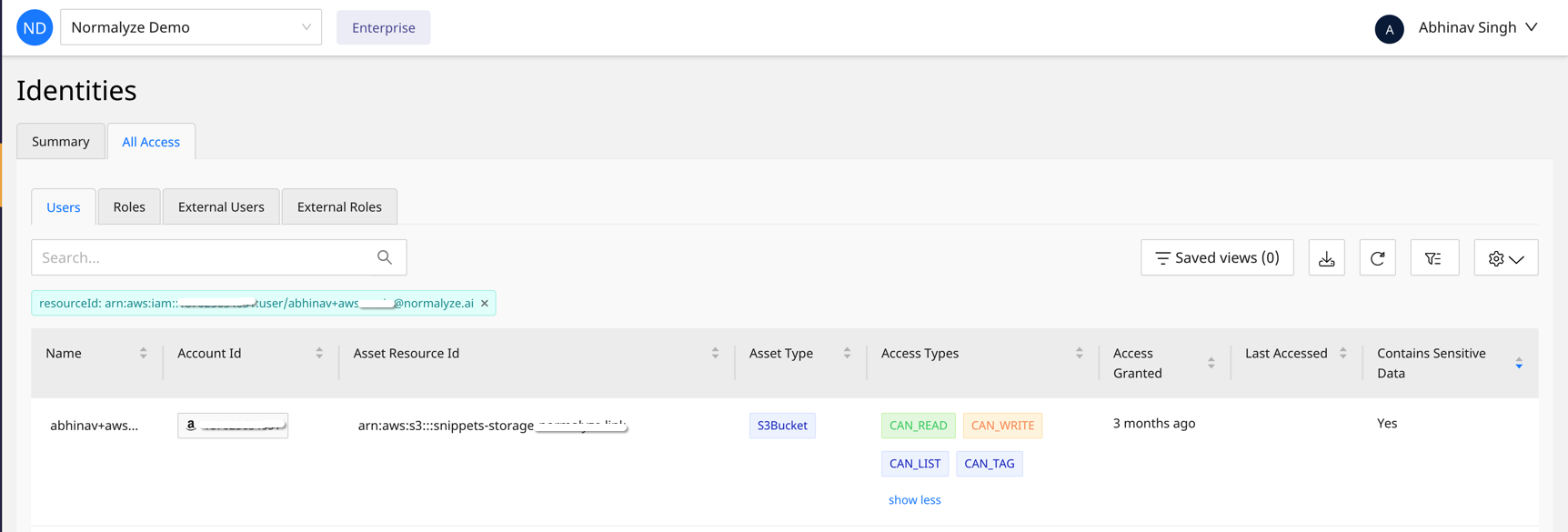
Auditing and monitoring the usage of IAM users and roles helps identify dormant or abandoned priviliges. Figure 1 below shows that a user was granted read and write access to a sensitive S3 bucket three months ago but the permissions were never used. Information like this can be used to remove overprovisioned permissions and lower the potential of sensitive data exposure.
Figure 1: Normalyze Identity dashboard, highlighting a privileged user with types of access to a sensitive datastore
2. Rapid incident response guided by data classification and risk-chain mapping
The second aspect pertains to identifying and categorizing sensitive data stored in the cloud. Data classification enables security teams to better understand critical data stores and the associated user roles.
In the LastPass case study, sensitive data stores containing Personally Identifiable Information (PII) and critical customer data should have been classified accordingly and accompanied by an access table or graph highlighting the users and roles with direct or indirect access to the cloud-resident sensitive information.
Data classification details like this can help security teams predict a chain of risky configurations that would otherwise look completely benign without the context of the data sensitivity information. A map of chained configurations is the attack path most likely to be used by cybercriminals.
Coupling such details with forensic metadata such as access-granted time and last accessed time can help accelerate the incident-response process.
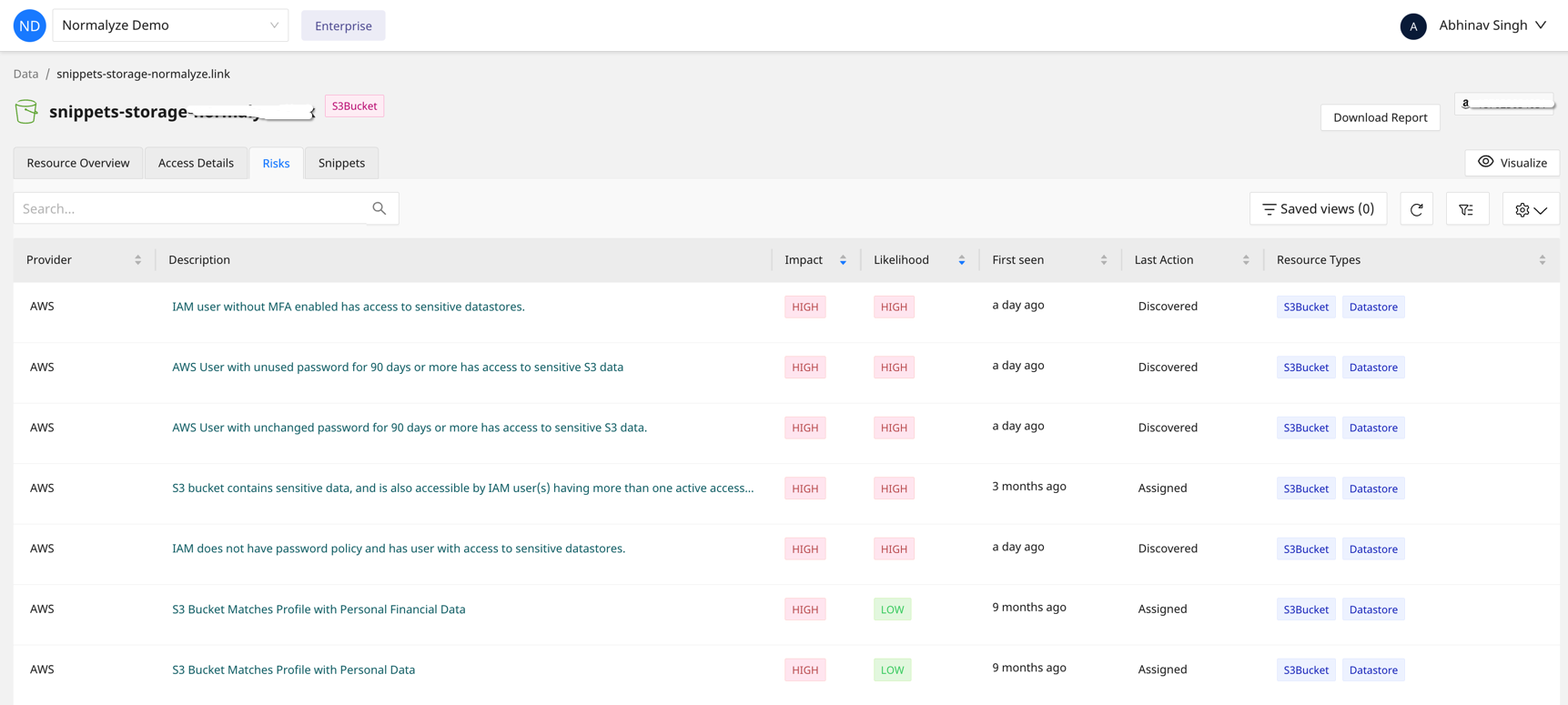
Figure 2: Normalyze dashboard highlighting risks associated with a sensitive datastore
Identification of risk chains of events leading to the exposure of sensitive datastores is done by combining Identity, configuration and real-time events happening in the data store. With a graphical view of all the risks associated with the datastore, security teams can quickly prioritize and remediate the gaps.
3. Be alert to abnormal behavior by tracking cloud data
The LastPass attacker exfiltrated a good chunk of encrypted and unencrypted data from the compromised cloud environment. Had effective monitoring been used, the data security team could have detected this anomaly.
From a lesson perspective, in the context of highly-sensitive data, organizations should have the means to monitor the environment for events such as structured data queries returning an extremely high count of matching results, IAM user-related events pointing to a sizable encrypted data dump/download, backups and snapshots shared cross-account, and so forth.
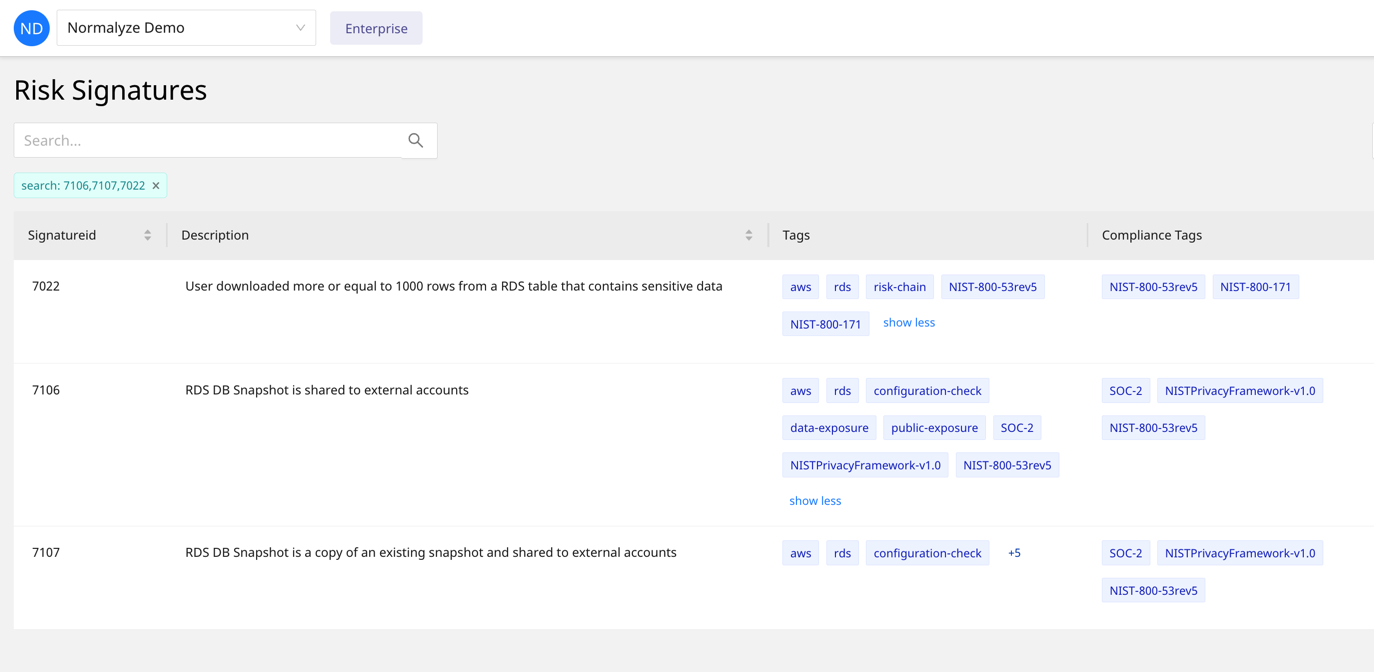
Figure 3: Examples of data movement risk types
Attacks have been reported in which data exfiltration adapted clever approaches, such as building a trust relationship with an external storage account by creating an S3 bucket Access Control List to enable cross-account object replication. Another example is using the cloud infrastructure backbone for a stealthier exfiltration by copying an Amazon Relational Database Service snapshot to a different AWS account.
To prevent sophisticated cyber attacks like these, organizations need a reliable tool for tracking anomalous behavior for their cloud-resident sensitive data.
Summary
The LastPass breaches were potentially affected at least 33 million users and 85,000 businesses worldwide. We have shared three lessons from these breaches that serve as a wake-up call for every organization storing sensitive data in public clouds. Prevention of breaches like these requires the use of effective tools and processes for securing cloud-resident sensitive data. Ignoring such security processes raises the risk level of exposure of user data.