Corelight transforms
data security with
Normalyze
When organizations need to know not only what type of malicious activity potentially occurred within their networks and clouds but also gather the remnants of that activity as evidence — they turn to Corelight. Corelight’s customers include Fortune 500 companies, major government agencies, and large research universities. Based in San Francisco, this open-core security company was founded by the creators of the widely-used network security technology, Zeek.
Data security is so challenging today that even sophisticated security companies like Corelight require external support to remain diligent and comprehensive in their security strategies. As the company’s first CISO, Bernard Brantley explains he needed to develop Corelight’s data security strategy and vision but also strengthen the company’s ability to execute that strategy. Brantley’s view on data security is a battle for information superiority and vision but also strengthen the company’s ability to execute that strategy. Brantley’s view on data security is a battle for information superiority and decision advantage over the adversaries that target their systems and information.
That’s why one of the first steps he took as CISO to defend that data was essential.
www.corelight.com
Industry: Information Technology
Size: 200 employees
Business Problem
Corelight’s CISO needed to increase visibility into Corelight’s cloud data and cloud environment risk posture. This visibility would help the team to reach and maintain the most-effective security capabilities to protect its data and cloud systems, as well as enable the security team to detect and effectively respond to potential security incidents.
Solution
With the Normalyze, Corelight and their security team can now continuously discover sensitive information, determine relevant attack paths, and automate the necessary remediation efforts to secure their data. Normalyze assessments will find enterprise structured and unstructured data, and Corelight can use Normalyze’s predefined compliance profiles to detect personally identifiable information (PII) and data that falls under regulatory mandates.
Why Corelight Chose Normalyze
- Normalyze assessments instantly identify sensitive structured and unstructured data.
- Normalyze’s context-aware data security insights drives better security decision-making.
- Normalyze Graph determines relevant attack paths that place data at-risk.
Effective data security demands
comprehensive visibility
Brantley’s primary objective as CISO was to ensure visibility into the risk posture of Corelight’s data capabilities to protect our data and cloud environment. “Not only would this help us to reach and maintain effective security and systems, but it would also enable us to detect and effectively respond to potential anomalies when necessary,” says Brantley. Such visibility would also enable Brantley and the team to accurately provide executives with the details necessary to communicate the value of their security program and regulatory compliance efforts, Brantley explains.
The lack of comprehensive visibility into the locations of their sensitive data, business-technology assets, as well as the access and configurations of their cloud access stood as the most pressing initial challenge facing Brantley and the Corelight security team. To get this information, the team could gather the data manually from their engineering, operations, and application teams and scour through their access logs and security and operations dashboards — but it would be highly time-consuming and neither effective nor efficient. The team could have also turned to an opensource tool and spent considerable resources on getting the application up and running and customized to the point that it could provide the level of visibility he and the team sought. “The reality is that we don’t have the size or team composition necessary to dedicate to building and maintaining the open-source solution. I needed to know how we could scale into such a platform, and I didn’t have an answer for that,” he says.
Another option? Turn to a standard cloud security posture management tool. “But that, too, would take considerable work to get to the point we needed,” explains Brantley. It’d also not provide the customizability and comprehensive details he sought. Before selecting a technology to support the data security program directly, Brantley hired a governance, risk, and compliance director to help him develop and structure the program. “We develop a very targeted program, and nail down al of our security and compliance objectives and identify the correct technical controls,” he says. The next objective would be finding a set of tools or program, that could help the team identify structured and unstructured data, assets, and their security configurations.
After carefully considering the available options, Brantley turned to recently-launched cloud data security provider, Normalyze. “Normalyze’s data-centric vision mirrored my long-term data security vision perfectly. That vision is to have comprehensive situational and structural awareness, specifically context about how that awareness supports better security decision-making,” he says. With Normalyze, Brantley would achieve a much better cloud data security posture than other enterprise cloud asset and visibility tools.

“Normalyze’s data-centric vision mirrored my long-term data security vision perfectly. That vision is to have comprehensive situational and structural awareness, specifically context about how that awareness supports better security decision-making.”
Bernard Brantley
Corelight CISO
Swift Time to Value with
Normalyze
One of Brantley’s most significant benefits from Normalyze is the knowledge graph that powers the platform. The Normalyze Graph, based on the findings from the Normalyze one-pass scanner, connects all enterprise data with its associated assets, identities, and their access to that data, as well as misconfigurations and vulnerabilities that place that data at risk.
With the Normalyze Graph, organizations such as Corelight and their security teams can continuously discover sensitive information, determine relevant attack paths, and automate the necessary remediation efforts to secure their data. In addition to finding structured and unstructured data, organizations can also use predefined compliance profiles within Normalyze to detect personally identifiable information (PII), the General Data Protection Regulation (GDPR), the Health Insurance Portability and Accountability Act (HIPAA), and more to ensure sensitive data never leaves their cloud environments.
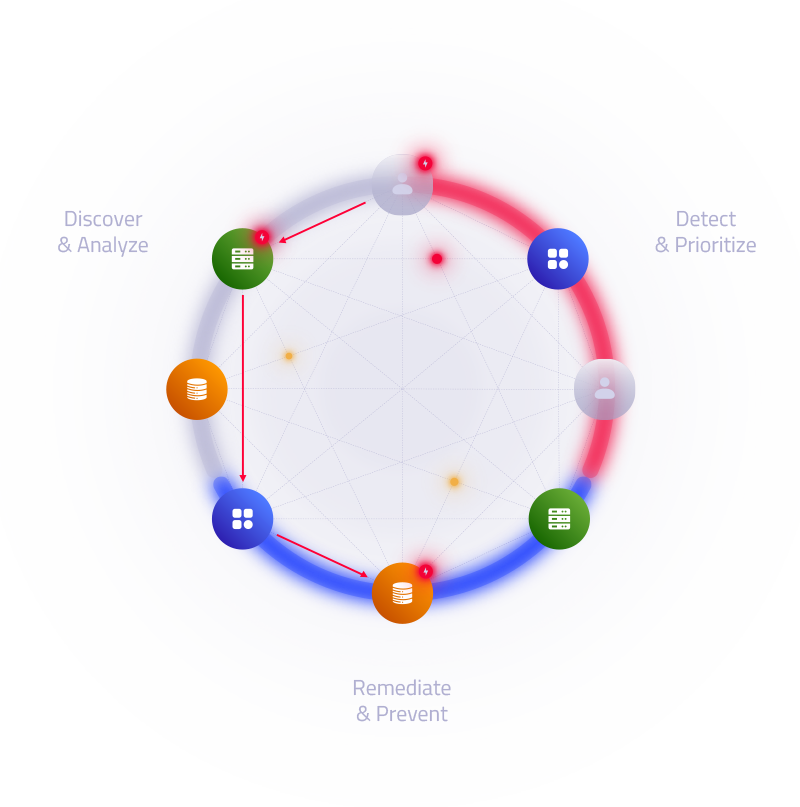
Additionally, the Normalyze Graph is equally valuable to the CISO as it is to the security engineer, analyst, DevOps professionals, and more as a way to discover data, classify its risk and attack paths, and remediate risks. The Normalyze data-first cloud security platform operates in three essential phases:
Discovery and Analysis
Normalyze builds an intelligent graph with deep context and transitive trust relationships that represent all the data stores, applications, identities, and infrastructure resources in all clouds and understands how they connect. The Normalyze agentless data scanner then determines what data-stores house sensitive information and automatically maps it to specific security policy and regulatory compliance profiles.
Detection and Prioritization
The Normalyze prioritization engine identifies risk paths discovered through the graph and prioritizes them based on the sensitivity of the data at risk and the attack’s impact.
Remediation and Prevention
Normalyze integrates with various external tools for notification, ticket creation, workflow triggering, and more so that users can automate remediation through their orchestration engine.

“The identification of sensitive data in places we did not know it was before is a testament to Normalyze’s capabilities. Now, when asked how teams are storing data and what controls they have for deleting or removing that data, we can see if they are following policy, and we will know if sensitive data shows up somewhere it shouldn’t, and we can then go work with the team immediately to remediate that.”
Bernard Brantley
Corelight CISO
A Comprehensive View
of Data and Associated Risk
Following the deployment of Normalyze, Brantley quickly identified the locations of Corelight’s sensitive data, and he could even spot data in areas they did not anticipate it existed. “We were able to review with the data owners the nature of the data that was making it to certain cloud storage locations. The data being there turned out to be a surprise to the team,” Brantley says.
“The identification of sensitive data in places we did not know it was before is a testament to Normalyze’s capabilities,” he says. “Now when asked how teams are storing data and what controls they have for deleting or removing that data, we can see if they are following policy, and we will know if sensitive data shows up somewhere it shouldn’t, and we can then go work with the team immediately to remediate that,” he adds.
Furthermore, with Normalyze’s timed data assessments, Brantley and the team will know whenever a weakness surfaces that could lead to a data breach and automatically dispatch a service ticket to ensure that situations that place data at risk are fixed swiftly.
The Normalyze Graph Provides the Single Pane of Glass
Perhaps most important to Brantley is how the Normalyze Graph provides him the comprehensive insights he needs into where sensitive data resides and how well it’s protected throughout their cloud environments. “It’s one of those tools that enables me to focus on defending and protecting data and systems rather than respond, which is much better from a risk perspective. The more efficiently I’m running my program, the more we stay ahead of potential issues in our interaction throughout the business,” he says.
“There are two extremely important things that Normalyze solves,” explains Brantley. “The first is: do I know where everything resides and how the systems are configured? Second: do I clearly understand the risk facing that data and systems? Normalyze presents me with these views.”
Shortly, Corelight will increase its use of Normalyze. “I’m going to ensure everybody who owns a cloud account or manages resources within a cloud account has the knowledge that Normalyze exists and fully understands its value,” he says.
Contact Us
We thrive on innovation, collaboration, transparency and building great tech, while having fun and creating a community around our customers, partners and employees.
