Analysis of a recent supply chain attack revealed that threat actors had seized control of an expired Amazon S3 bucket that hosted binaries necessary for the npm package bignum. Bignum is an npm package that uses OpenSSL for arbitrary precision integral arithmetic. The npm package leveraged node-pre-gyp to download a pre-built binary file during installation. This attack is unprecedented due to a combination of cloud misconfigurations that led to the supply chain compromise. This technique can open up avenues for further attacks in the future, primarily where cloud storage services are used to host the content of open-source libraries.
Executive Summary
The older versions of the bignum package, from v0.12.2 to v0.13.0 (inclusive), relied on the S3 bucket to download pre-built versions of the add-on. The latest version did not support downloading pre-built binaries; therefore, the bucket was deleted by the developers of the module. This gave the attacker a perfect opportunity to replace the deleted bucket with one they could control. The binary file code was then modified to add a malicious payload while still serving the expected functionality. Applications and services still relying on the older versions of bignum would end up installing the infected version of the binary, thus compromising the software supply chain.
The challenge for security teams is to identify and address expired buckets that create security issues and ignore those that don’t. To make that distinction requires an understanding of the context of the buckets in the cloud environment. Normalyze, as a robust DSPM solution, establishes a vital link between resource misconfigurations and your sensitive data, enabling a comprehensive analysis of both direct and indirect exposure risks. With this powerful connection, you gain valuable insights into the security of your sensitive data, ensuring enhanced protection and compliance.
The Mechanics of the Attack
This attack uses the Subdomain Takeover Technique (MITRE ID: T1584.001). In this attack, the adversary takes control of an organization’s hosted subdomain via cloud services like AWS or Azure. The basic premise involves a DNS record entry pointing to non-existing or deprovisioned resources. This allows attackers to create a new resource (e.g., S3 bucket) with the same name. The new subdomain requests are routed to the attacker-controlled resource, allowing them to steal valuable information, as depicted in Figure 1.
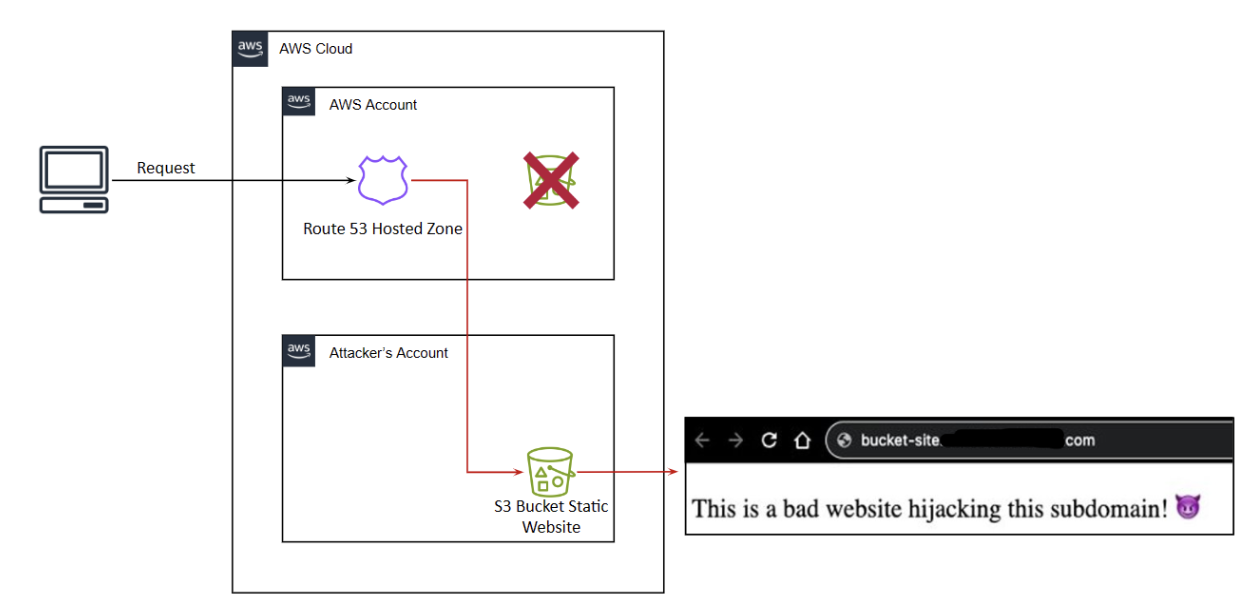
Figure 1: Demonstration of a Subdomain Takeover attack in the cloud.
Figure 2 shows how the attack unfolded. Installing the older, impacted versions of the bignum package sent a request to the original S3 bucket, which was instead redirected to the hijacked bucket so the malicious file could be sent to the requestor.
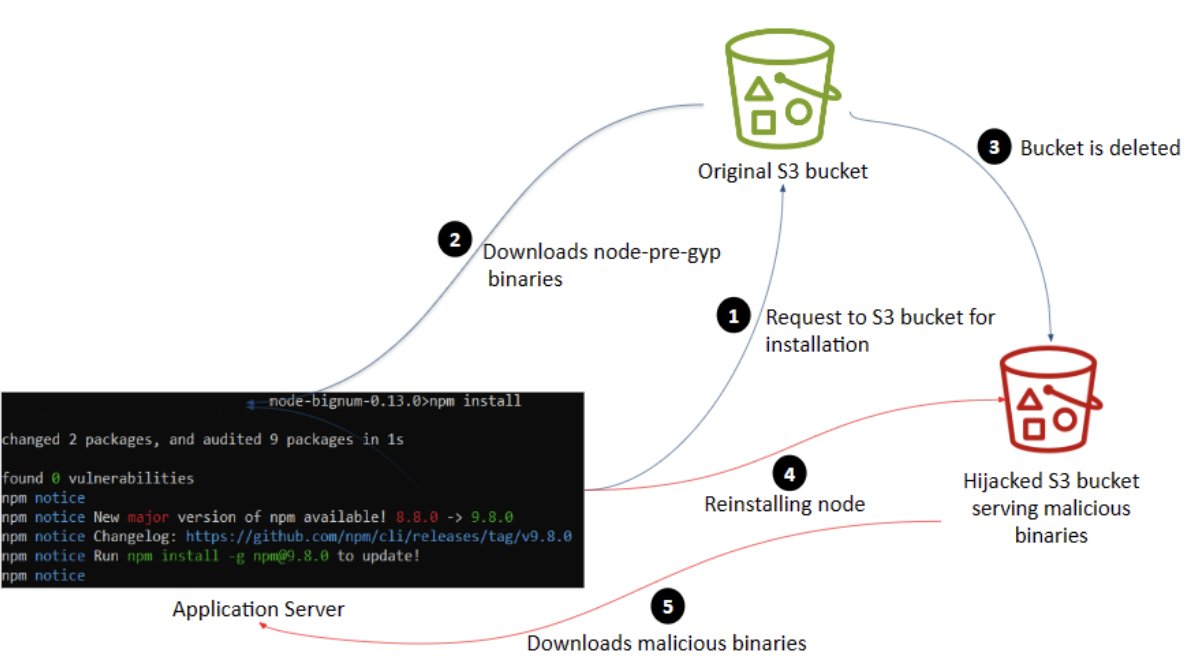
Figure 2: Understanding the Cloud-Supply chain attack vector.
The malicious binary file would be downloaded, which would then steal user ids, passwords, local environment variables, etc., and exfiltrate the stolen data to the hijacked bucket.
During the investigation, it was found that https://rvagg-node[.]s3-us-west-2.amazonaws.com is most likely the Amazon S3 bucket that was being used for storing binaries of the impacted version of node-bignum. This bucket is now inaccessible.
Scanning the malicious binary on VirusTotal produces results and is flagged by a long list of vendors as malicious, as shown in Figure 3.

Figure 3: VirusTotal Score for the malicious binary.
How Normalyze Protects Against Subdomain Takeover
With Normalyze, organizations can determine the risk of attacks like these, visualize their cloud data within minutes, and get real-time visibility and control into their security posture, including access, configurations, and sensitive data to secure cloud infrastructures at scale.
A risk identified by the Normalyze platform, as shown in figure 4 below, highlights subdomain takeover vulnerabilities that affect AWS Route53. It also provides detailed remediation steps on how the risk can be quickly remediated from the infrastructure either using the cloud command-line, through the cloud console UI or through an Infrastructure-as-code (e.g., Terraform) script.
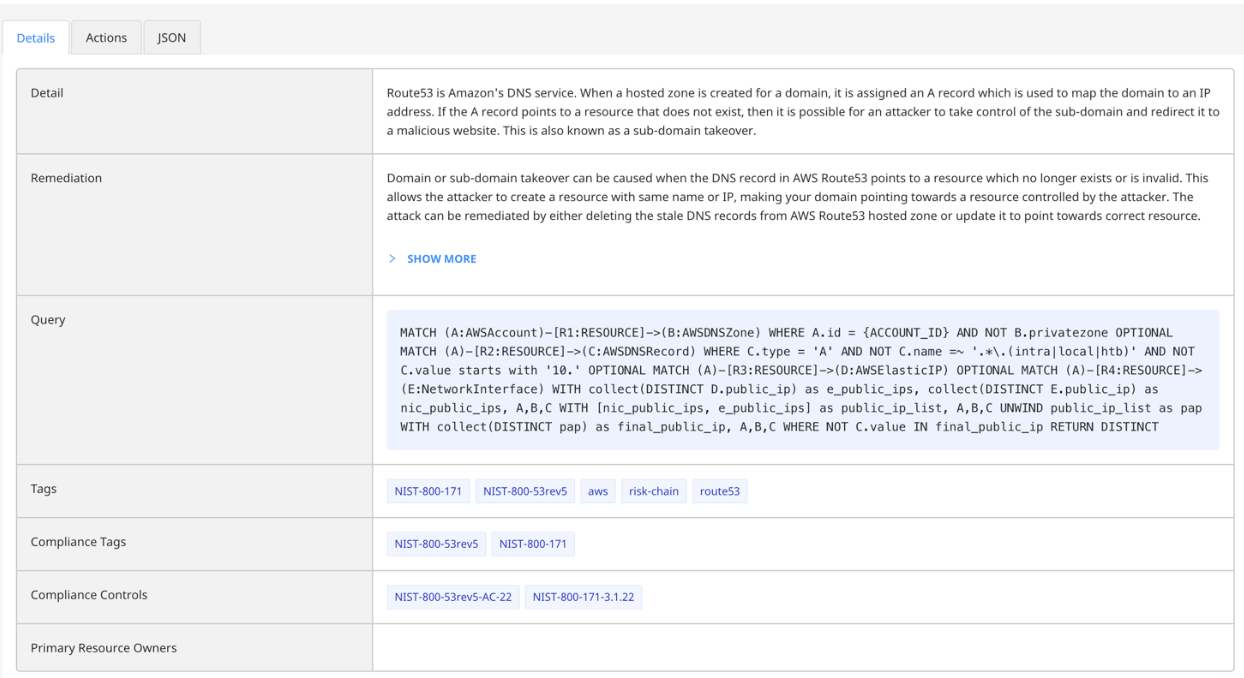
Figure 4: Details of the risk detection for subdomain takeover in the Normalyze platform.
Additional details of the risk contains information about the misconfigured cloud resource. In this case, it will be the resource that is responsible for maintaining the DNS settings in your cloud infrastructure, for example AWS Route 53 or Azure DNS service. Normalyze also identifies the actual DNS entry which is exposed through this risk, along with additional properties of the record.
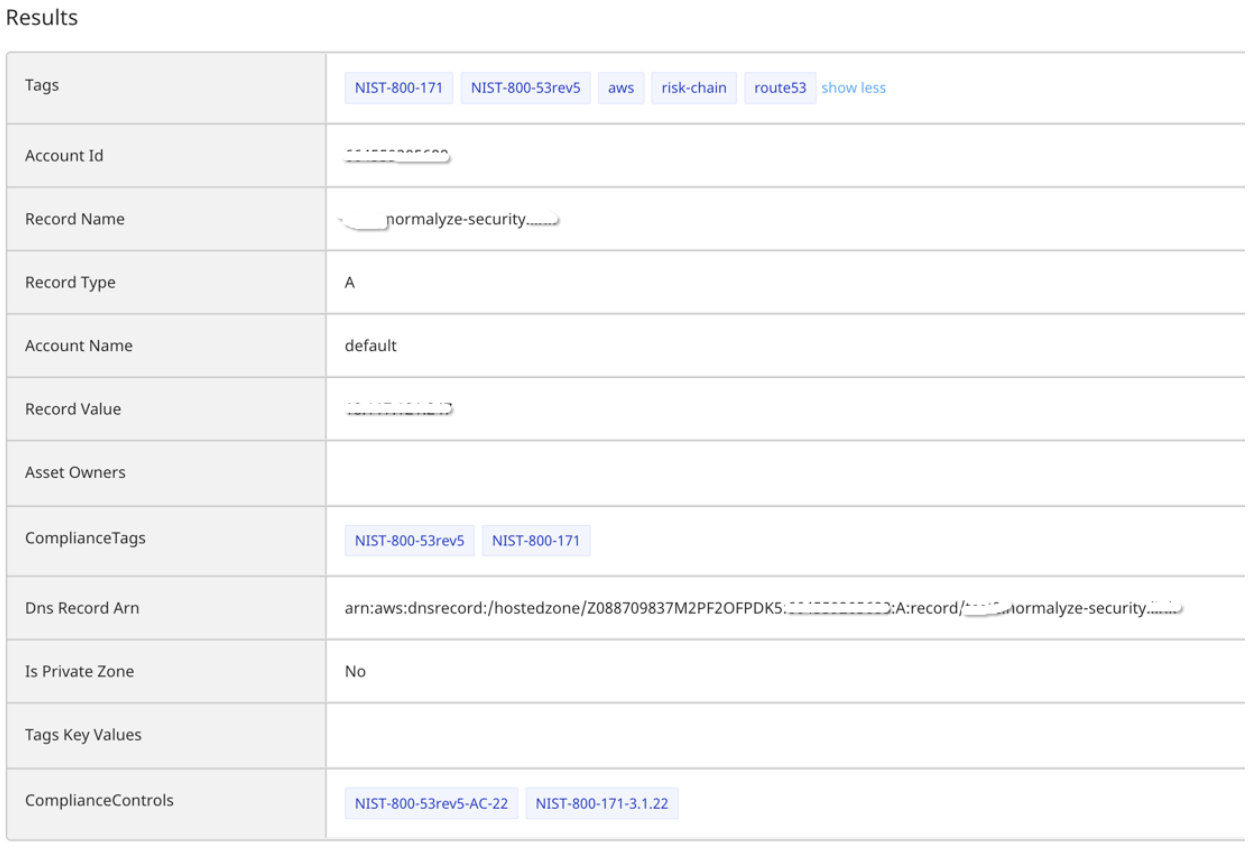
Figure 5: Risk Result page highlighting the properties of the misconfigured cloud resource.
In the next phase, you can leverage the Risk Actions tab to promptly notify your Security and DevSecOps team, or seamlessly relay the findings to downstream systems, such as SIEM, incident management, and ticketing platforms like Slack or Jira.
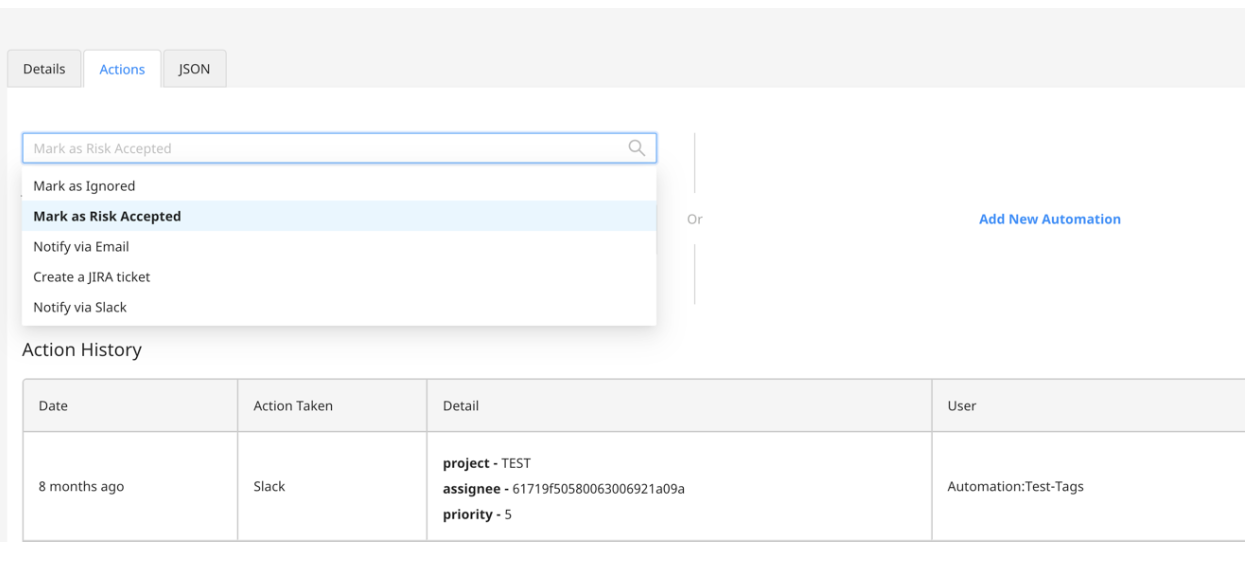
Figure 6: Risk automation for faster response and remediation
Try Normalyze in Your Environment
The Normalyze agentless scanning platform continuously discovers resources, sensitive data, and access paths across all cloud environments. To see it in action, get a demo of the Normalyze DSPM platform!
Indicators Of Compromise
- 1. Bucket URL: https://rvagg-node[.]s3-us-west-2.amazonaws.com
- 2. Malicious binary hash(SHA256): 3c6793de04bfc8407392704b3a6cef650425e42ebc95455f3c680264c70043a7
- 3. Vulnerable package versions: Bignum >= 0.12.2, < 0.13.1




