
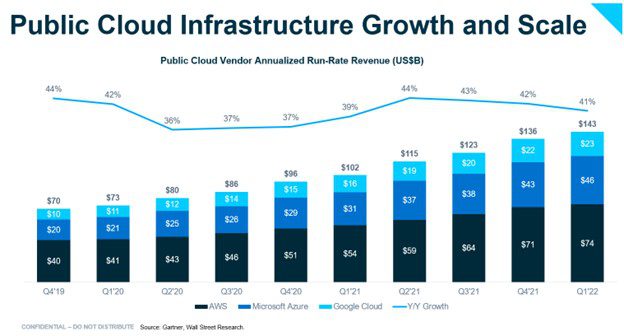
The shift to the cloud is upending the compute model from one that is resource/application-centric to one that is data-centric. Cloud platforms like AWS, Azure and Google have abstracted away the need to manage databases, compute resources and networks for where applications run. Similarly, managed datastores like Snowflake, Databricks* and MongoDB have unleashed the ability for enterprises to operationalize data in applications or for internal use cases. The adoption of public cloud services has surged over the past few years, with spending on public cloud infrastructure at $143 billion growing 41% Y/Y, according to Gartner. As such, the need to secure data across heterogeneous environments is becoming a critical pillar of security programs as data becomes the core differentiating resource among enterprises.
The shift to the cloud is upending the compute model from one that is resource/application-centric to one that is data-centric. Cloud platforms like AWS, Azure and Google have abstracted away the need to manage databases, compute resources and networks for where applications run. Similarly, managed datastores like Snowflake, Databricks* and MongoDB have unleashed the ability for enterprises to operationalize data in applications or for internal use cases. The adoption of public cloud services has surged over the past few years, with spending on public cloud infrastructure at $143 billion growing 41% Y/Y, according to Gartner. As such, the need to secure data across heterogeneous environments is becoming a critical pillar of security programs as data becomes the core differentiating resource among enterprises.
Enter Normalyze*
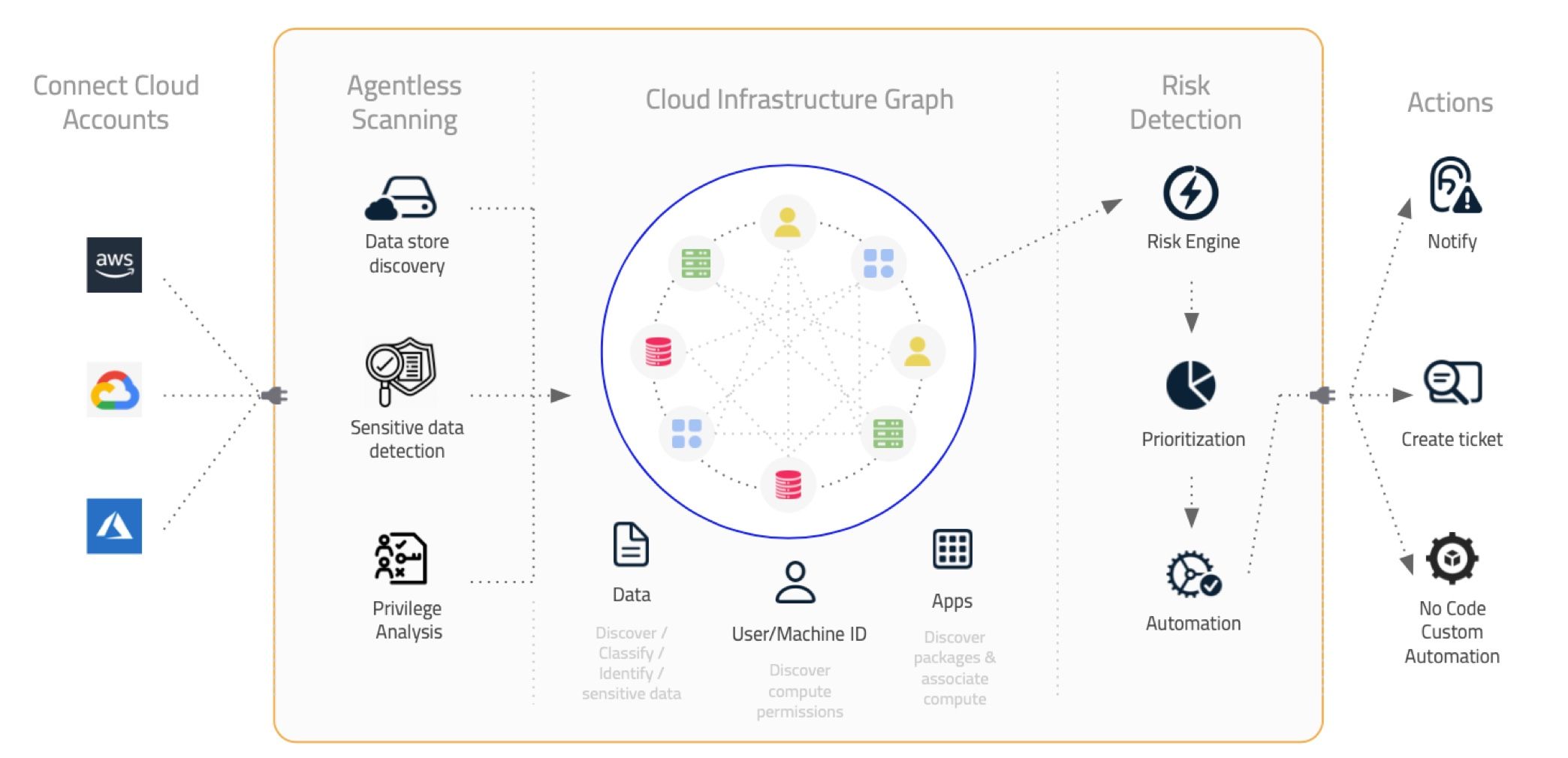
Founded in December 2020 by Ravi Ithal, co-founder and chief architect at Netskope, and Amer Deeba, a long-time executive at Qualys and Moogsoft with deep roots in scaling high-velocity, go-to-market teams, Normalyze is an agentless cloud data-security platform. The product gives users a full picture of their data stores, applications, identities, infrastructure, and how they are all connected. Core to the platform are its discovery and classification, detection, and remediation capabilities, which give DevOps and security engineers visibility into their data sprawl, the relationships between their infrastructure, applications, and users, and the automation capability to detect and remediate issues in real-time. By tying together these assets in a graph-powered platform, Normalyze is able to uniquely categorize risk based on relationships and allow DevSecOps teams to traverse attack paths to sensitive information.
Since its inception the company has assembled a team of 20+ engineers across the U.S. and India, and its product is already being deeply used by customers in production. Normalyze’s time-to-value is an important driver of its rapid adoption over the past several months, and we believe the team has built the only data-security platform that has been architected to meet the needs of individual practitioners and teams alike.
At Battery, we get excited when founders and entrepreneurs approach complex problems with first-principles thinking, simplicity and clarity. Amer, Ravi and the rest of the Normalyze team bring a wealth of knowledge from their time spent at Netskope and Qualys and understand how to bring clarity to security’s most complex problem—data.
We have been fortunate to partner with category-defining data platforms like Databricks*, Matillion*, Streamsets*, InfluxData* and Collibra*, as well as security companies like Splunk*, Akamai*, Sumo Logic*, Bionic*, Contrast Security*, Styra* and Bridgecrew*–and now we’re excited to be a part of the journey for Normalyze to redefine data security for the cloud era.



